diff --git a/_partials/_transit-gateway-aws.md b/_partials/_transit-gateway-aws.md
new file mode 100644
index 0000000000..2c4cb51f1e
--- /dev/null
+++ b/_partials/_transit-gateway-aws.md
@@ -0,0 +1,43 @@
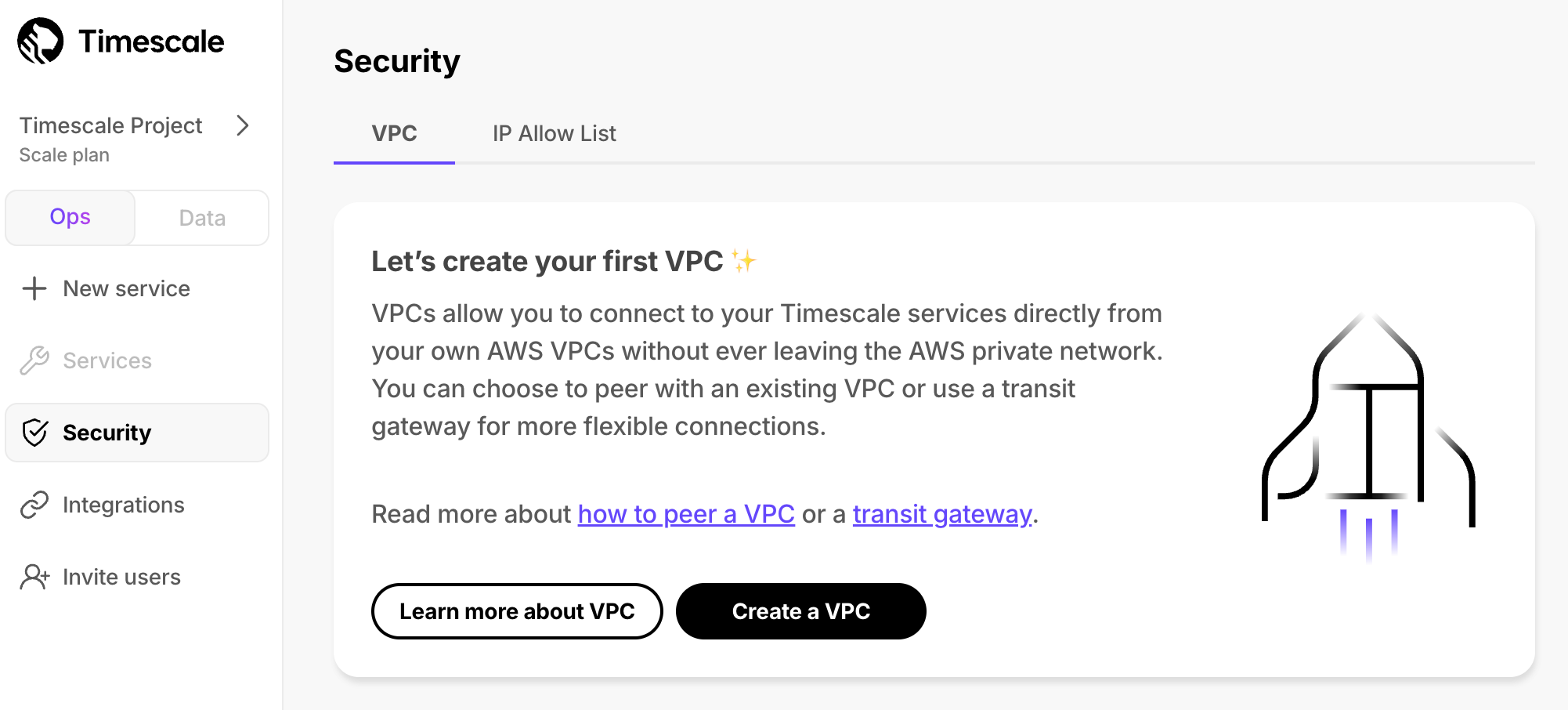
+1. **Create a Peering $VPC in [$CONSOLE][console-login]**
+
+ 1. In `Security` > `VPC`, click `Create a VPC`:
+
+ 
+
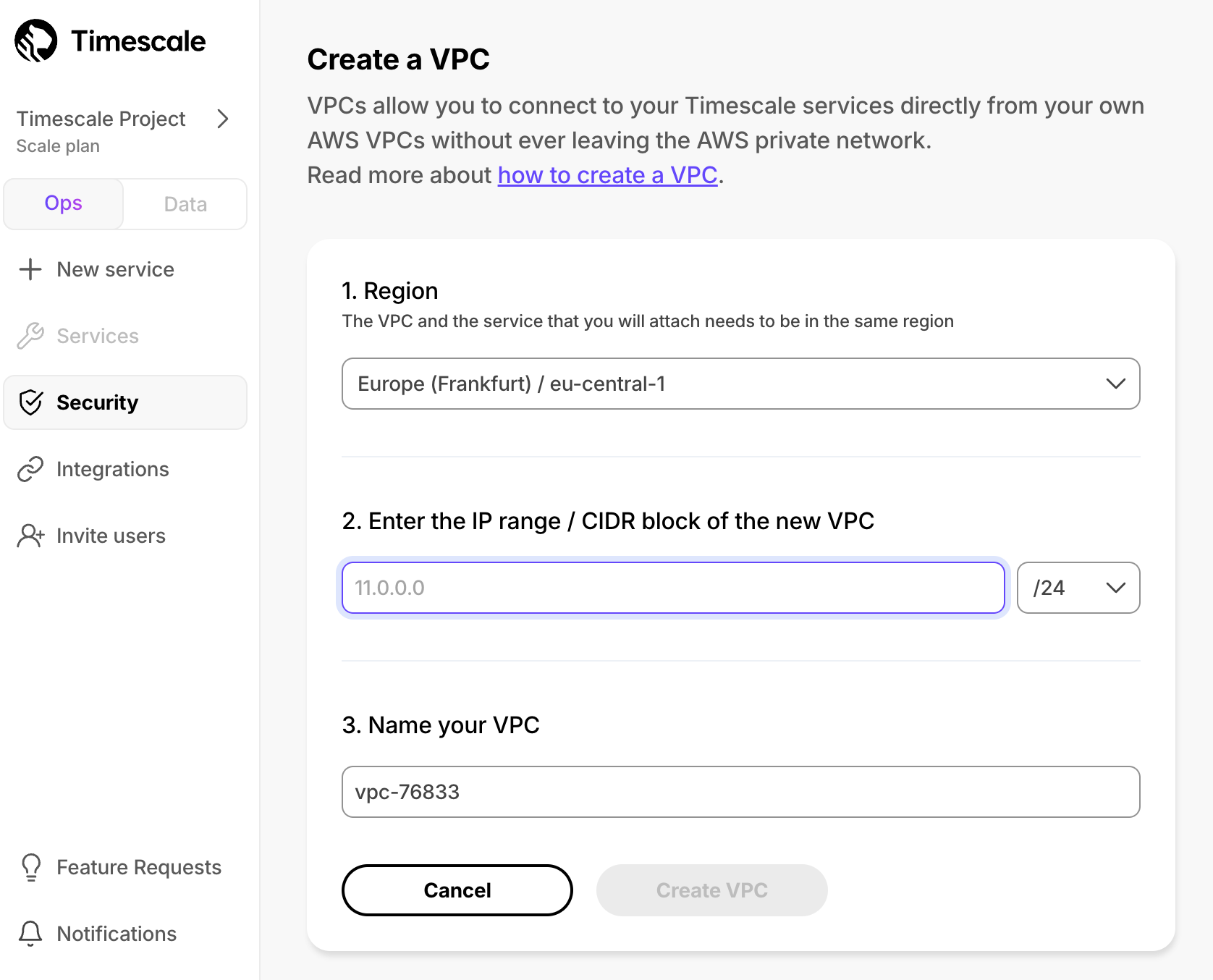
+ 1. Choose your region and IP range, name your VPC, then click `Create VPC`:
+
+ 
+
+ Your $SERVICE_SHORT and Peering $VPC must be in the same AWS region. The number of Peering $VPCs you can create in your project depends on your [price tier][pricing-plans]. If you need another Peering $VPC, either contact [support@timescale.com](mailto:support@timescale.com) or change your tier in [$CONSOLE][console-login].
+
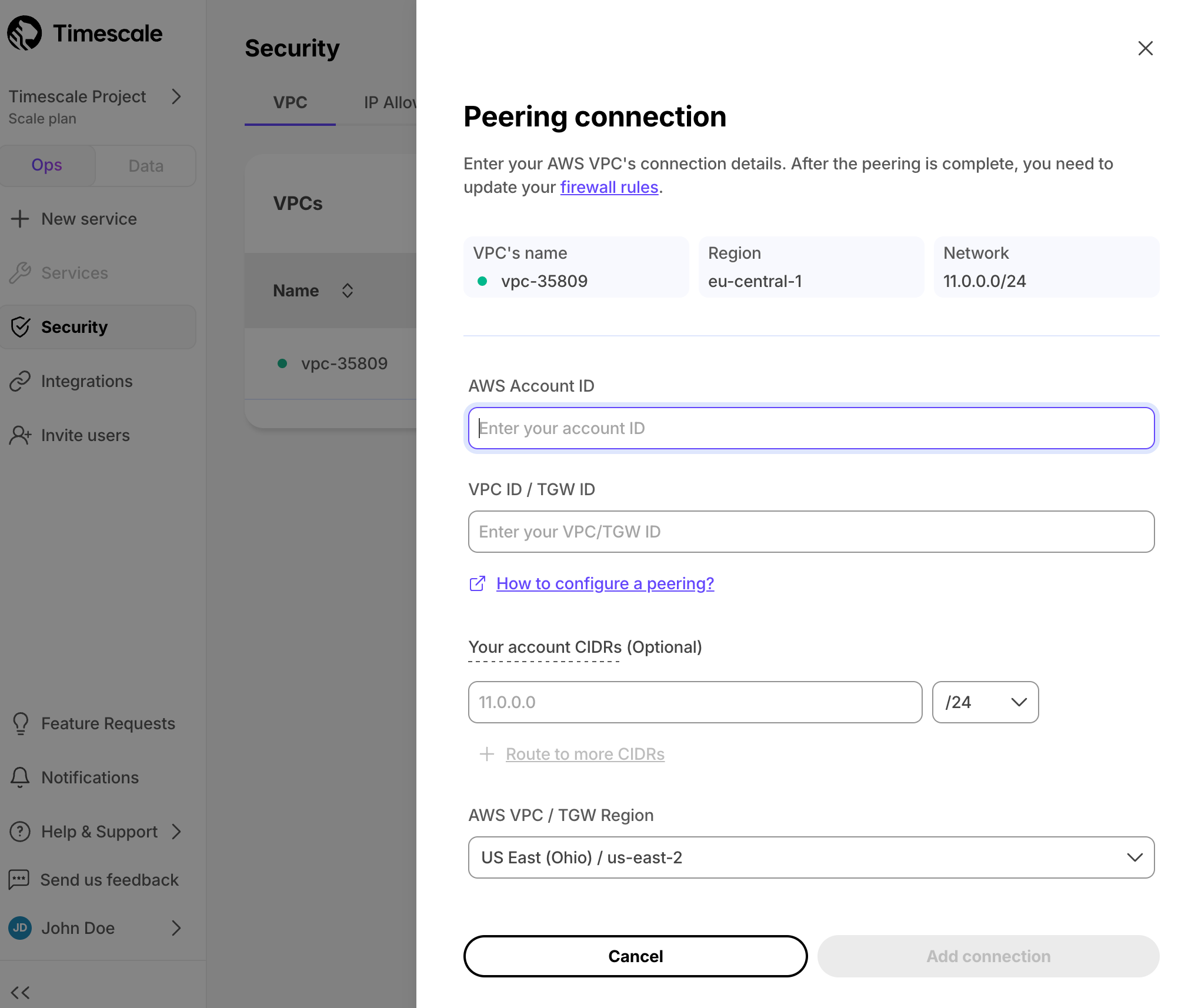
+ 1. Add a peering connection:
+
+ 1. In the `VPC Peering` column, click `Add`.
+ 1. Provide your AWS account ID, Transit Gateway ID, CIDR ranges, and AWS region.
+ 1. Click `Add connection`.
+
+ 
+
+1. **Accept and configure peering connection in your AWS account**
+
+ Once your peering connection appears as `Processing`, you can accept and configure it in AWS:
+
+ 1. Accept the peering request coming from $CLOUD_LONG. The request can take up to 5 min to arrive. Within 5 more minutes after accepting, the peering should appear as `Connected` in $CONSOLE.
+
+ 1. Configure at least the following in yur AWS account networking:
+
+ - Your subnet route table to route traffic to your Transit Gateway for the Peering VPC CIDRs.
+ - Your Transit Gateway route table to route traffic to the newly created Transit Gateway peering attachment for the Peering VPC CIDRs.
+ - Security groups to allow outbound TCP 5432.
+
+1. **Attach a $CLOUD_LONG service to the Peering VPC In [$CONSOLE][console-services]**
+
+ 1. Select the $SERVICE_SHORT you want to connect to the Peering VPC.
+ 1. Click `Operations` > `Security` > `VPC`.
+ 1. Select the VPC, then click `Attach VPC`.
+
+ You cannot attach a $SERVICE_LONG to multiple $CLOUD_LONG $VPCs at the same time.
+
+[console-login]: https://console.cloud.timescale.com/
+[console-services]: https://console.cloud.timescale.com/dashboard/services
+[pricing-plans]: /about/:currentVersion:/pricing-and-account-management/
diff --git a/_partials/_transit-gateway-others.md b/_partials/_transit-gateway-others.md
new file mode 100644
index 0000000000..b11cea5367
--- /dev/null
+++ b/_partials/_transit-gateway-others.md
@@ -0,0 +1,43 @@
+2. **Create a Peering $VPC in [$CONSOLE][console-login]**
+
+ 1. In `Security` > `VPC`, click `Create a VPC`:
+
+ 
+
+ 1. Choose your region and IP range, name your VPC, then click `Create VPC`:
+
+ 
+
+ Your $SERVICE_SHORT and Peering $VPC must be in the same AWS region. The number of Peering $VPCs you can create in your project depends on your [price tier][pricing-plans]. If you need another Peering $VPC, either contact [support@timescale.com](mailto:support@timescale.com) or change your tier in [$CONSOLE][console-login].
+
+ 1. Add a peering connection:
+
+ 1. In the `VPC Peering` column, click `Add`.
+ 1. Provide your AWS account ID, Transit Gateway ID, CIDR ranges, and AWS region.
+ 1. Click `Add connection`.
+
+ 
+
+1. **Accept and configure peering connection in your AWS account**
+
+ Once your peering connection appears as `Processing`, you can accept and configure it in AWS:
+
+ 1. Accept the peering request coming from $CLOUD_LONG. The request can take up to 5 min to arrive. Within 5 more minutes after accepting, the peering should appear as `Connected` in $CONSOLE.
+
+ 1. Configure at least the following in yur AWS account networking:
+
+ - Your subnet route table to route traffic to your Transit Gateway for the Peering VPC CIDRs.
+ - Your Transit Gateway route table to route traffic to the newly created Transit Gateway peering attachment for the Peering VPC CIDRs.
+ - Security groups to allow outbound TCP 5432.
+
+1. **Attach a $CLOUD_LONG service to the Peering VPC In [$CONSOLE][console-services]**
+
+ 1. Select the $SERVICE_SHORT you want to connect to the Peering VPC.
+ 1. Click `Operations` > `Security` > `VPC`.
+ 1. Select the VPC, then click `Attach VPC`.
+
+ You cannot attach a $SERVICE_LONG to multiple $CLOUD_LONG $VPCs at the same time.
+
+[console-login]: https://console.cloud.timescale.com/
+[console-services]: https://console.cloud.timescale.com/dashboard/services
+[pricing-plans]: /about/:currentVersion:/pricing-and-account-management/
diff --git a/migrate/dual-write-and-backfill/dual-write-from-other.md b/migrate/dual-write-and-backfill/dual-write-from-other.md
index 9725cef8d4..c32b8e4210 100644
--- a/migrate/dual-write-and-backfill/dual-write-from-other.md
+++ b/migrate/dual-write-and-backfill/dual-write-from-other.md
@@ -137,4 +137,4 @@ your production workload.
-[dual-write-and-backfill]: /migrate/:currentVersion:/dual-write-and-backfill/
\ No newline at end of file
+[dual-write-and-backfill]: /migrate/:currentVersion:/dual-write-and-backfill/
diff --git a/use-timescale/integrations/aws.md b/use-timescale/integrations/aws.md
new file mode 100644
index 0000000000..c9bcf52a03
--- /dev/null
+++ b/use-timescale/integrations/aws.md
@@ -0,0 +1,33 @@
+---
+title: Integrate Amazon Web Services with Timescale Cloud
+excerpt: AWS enables you to build, run, and manage applications across cloud, hybrid, and edge environments with AI, analytics, security, and scalable infrastructure. Integrate AWS with Timescale Cloud using AWS Transit Gateway
+products: [cloud]
+keywords: [AWS, integrations]
+---
+
+import IntegrationPrereqsCloud from "versionContent/_partials/_integration-prereqs-cloud-only.mdx";
+import TransitGatewayAWS from "versionContent/_partials/_transit-gateway-aws.mdx";
+
+# Integrate Amazon Web Services with $CLOUD_LONG
+
+[Amazon Web Services (AWS)][aws] is a comprehensive cloud computing platform that provides on-demand infrastructure, storage, databases, AI, analytics, and security services to help businesses build, deploy, and scale applications in the cloud.
+
+This page explains how to integrate your AWS infrastructure with $CLOUD_LONG using [AWS Transit Gateway][aws-transit-gateway].
+
+## Prerequisites
+
+
+
+- Set up [AWS Transit Gateway][gtw-setup].
+
+## Connect your AWS infrastructure to your $SERVICE_LONGs
+
+To connect to $CLOUD_LONG:
+
+
+
+You have successfully integrated your AWS infrastructure with $CLOUD_LONG.
+
+[aws]: https://aws.amazon.com/
+[aws-transit-gateway]: https://aws.amazon.com/transit-gateway/
+[gtw-setup]: https://docs.aws.amazon.com/vpc/latest/tgw/tgw-getting-started.html
diff --git a/use-timescale/integrations/corporate-data-center.md b/use-timescale/integrations/corporate-data-center.md
new file mode 100644
index 0000000000..ff158d9496
--- /dev/null
+++ b/use-timescale/integrations/corporate-data-center.md
@@ -0,0 +1,35 @@
+---
+title: Integrate your data center with Timescale Cloud
+excerpt: Integrate your on-premise data center with Timescale Cloud using AWS Transit Gateway
+products: [cloud]
+keywords: [on-premise, integrations]
+---
+
+import IntegrationPrereqsCloud from "versionContent/_partials/_integration-prereqs-cloud-only.mdx";
+import TransitGatewayOthers from "versionContent/_partials/_transit-gateway-others.mdx";
+
+# Integrate your data center with $CLOUD_LONG
+
+This page explains how to integrate your corporate on-premise infrastructure with $CLOUD_LONG using [AWS Transit Gateway][aws-transit-gateway].
+
+## Prerequisites
+
+
+
+- Set up [AWS Transit Gateway][gtw-setup].
+
+## Connect your on-premise infrastructure to your $SERVICE_LONGs
+
+To connect to $CLOUD_LONG:
+
+1. **Connect your infrastructure to AWS Transit Gateway**
+
+ Establish connectivity between your on-premise infrastructure and AWS. See the [Centralize network connectivity using AWS Transit Gateway][aws-onprem].
+
+
+
+You have successfully integrated your Microsoft Azure infrastructure with $CLOUD_LONG.
+
+[aws-transit-gateway]: https://aws.amazon.com/transit-gateway/
+[gtw-setup]: https://docs.aws.amazon.com/vpc/latest/tgw/tgw-getting-started.html
+[aws-onprem]: https://docs.aws.amazon.com/prescriptive-guidance/latest/patterns/centralize-network-connectivity-using-aws-transit-gateway.html
diff --git a/use-timescale/integrations/google-cloud.md b/use-timescale/integrations/google-cloud.md
new file mode 100644
index 0000000000..e4777dcddb
--- /dev/null
+++ b/use-timescale/integrations/google-cloud.md
@@ -0,0 +1,38 @@
+---
+title: Integrate Google Cloud with Timescale Cloud
+excerpt: Google Cloud enables you to deploy, manage, and scale cloud-based applications, databases, and data processing workflows. Integrate Google Cloud with Timescale Cloud using AWS Transit Gateway
+products: [cloud]
+keywords: [Google Cloud, integrations]
+---
+
+import IntegrationPrereqsCloud from "versionContent/_partials/_integration-prereqs-cloud-only.mdx";
+import TransitGatewayOthers from "versionContent/_partials/_transit-gateway-others.mdx";
+
+# Integrate Google Cloud with $CLOUD_LONG
+
+[Google Cloud][google-cloud] is a suite of cloud computing services, offering scalable infrastructure, AI, analytics, databases, security, and developer tools to help businesses build, deploy, and manage applications.
+
+This page explains how to integrate your Google Cloud infrastructure with $CLOUD_LONG using [AWS Transit Gateway][aws-transit-gateway].
+
+## Prerequisites
+
+
+
+- Set up [AWS Transit Gateway][gtw-setup].
+
+## Connect your Google Cloud infrastructure to your $SERVICE_LONGs
+
+To connect to $CLOUD_LONG:
+
+1. **Connect your infrastructure to AWS Transit Gateway**
+
+ Establish connectivity between Google Cloud and AWS. See [Connect HA VPN to AWS peer gateways][gcp-aws].
+
+
+
+You have successfully integrated your Google Cloud infrastructure with $CLOUD_LONG.
+
+[google-cloud]: https://cloud.google.com/?hl=en
+[aws-transit-gateway]: https://aws.amazon.com/transit-gateway/
+[gtw-setup]: https://docs.aws.amazon.com/vpc/latest/tgw/tgw-getting-started.html
+[gcp-aws]: https://cloud.google.com/network-connectivity/docs/vpn/how-to/connect-ha-vpn-aws-peer-gateway
diff --git a/use-timescale/integrations/index.md b/use-timescale/integrations/index.md
index 774f9af2b5..369e1c05ca 100644
--- a/use-timescale/integrations/index.md
+++ b/use-timescale/integrations/index.md
@@ -45,6 +45,7 @@ Some of the most in-demand integrations for $CLOUD_LONG are listed below, with l
| [Terraform][terraform] | Safely and predictably provision and manage infrastructure in any cloud. |
+
## Data engineering and extract, transform, load
| Name | Description |
@@ -68,6 +69,16 @@ Some of the most in-demand integrations for $CLOUD_LONG are listed below, with l
| [Power BI][power-bi] | Visualize data, build interactive dashboards, and share insights. |
+## Secure connectivity to $CLOUD_LONG
+
+| Name | Description |
+|:------------------------------------:|-----------------------------------------------------------------------------|
+| [Amazon Web Services][aws] | Connect your other services and applications running in AWS to $CLOUD_LONG. |
+| [Google Cloud][google-cloud] | Connect your Google Cloud infrastructure to $CLOUD_LONG. |
+| [Microsoft Azure][azure] | Connect your Microsoft Azure infrastructure to $CLOUD_LONG. |
+| [Corporate data center][data-center] | Connect your on-premise data center to $CLOUD_LONG. |
+
+
[psql]: /use-timescale/:currentVersion:/integrations/psql/
[qstudio]: /use-timescale/:currentVersion:/integrations/qstudio/
[cloudwatch]: /use-timescale/:currentVersion:/integrations/cloudwatch/
@@ -88,4 +99,7 @@ Some of the most in-demand integrations for $CLOUD_LONG are listed below, with l
[amazon-sagemaker]: /use-timescale/:currentVersion:/integrations/amazon-sagemaker
[postgresql]: /use-timescale/:currentVersion:/integrations/postgresql
[kafka]: /use-timescale/:currentVersion:/integrations/apache-kafka
-
+[aws]: /use-timescale/:currentVersion:/integrations/aws
+[google-cloud]: /use-timescale/:currentVersion:/integrations/google-cloud
+[azure]: /use-timescale/:currentVersion:/integrations/microsoft-azure
+[data-center]: /use-timescale/:currentVersion:/integrations/corporate-data-center
\ No newline at end of file
diff --git a/use-timescale/integrations/microsoft-azure.md b/use-timescale/integrations/microsoft-azure.md
new file mode 100644
index 0000000000..6686a802e6
--- /dev/null
+++ b/use-timescale/integrations/microsoft-azure.md
@@ -0,0 +1,38 @@
+---
+title: Integrate Microsoft Azure with Timescale Cloud
+excerpt: Microsoft Azure enables you to build, deploy, and manage applications across cloud, hybrid, and edge environments. Integrate Microsoft Azure with Timescale Cloud using AWS Transit Gateway
+products: [cloud]
+keywords: [Azure, integrations]
+---
+
+import IntegrationPrereqsCloud from "versionContent/_partials/_integration-prereqs-cloud-only.mdx";
+import TransitGatewayOthers from "versionContent/_partials/_transit-gateway-others.mdx";
+
+# Integrate Microsoft Azure with $CLOUD_LONG
+
+[Microsoft Azure][azure] is a cloud computing platform and services suite, offering infrastructure, AI, analytics, security, and developer tools to help businesses build, deploy, and manage applications.
+
+This page explains how to integrate your Microsoft Azure infrastructure with $CLOUD_LONG using [AWS Transit Gateway][aws-transit-gateway].
+
+## Prerequisites
+
+
+
+- Set up [AWS Transit Gateway][gtw-setup].
+
+## Connect your Microsoft Azure infrastructure to your $SERVICE_LONGs
+
+To connect to $CLOUD_LONG:
+
+1. **Connect your infrastructure to AWS Transit Gateway**
+
+ Establish connectivity between Azure and AWS. See the [AWS architectural documentation][azure-aws] for details.
+
+
+
+You have successfully integrated your Microsoft Azure infrastructure with $CLOUD_LONG.
+
+[aws-transit-gateway]: https://aws.amazon.com/transit-gateway/
+[gtw-setup]: https://docs.aws.amazon.com/vpc/latest/tgw/tgw-getting-started.html
+[azure]: https://azure.microsoft.com/en-gb/
+[azure-aws]: https://aws.amazon.com/blogs/modernizing-with-aws/designing-private-network-connectivity-aws-azure/
diff --git a/use-timescale/page-index/page-index.js b/use-timescale/page-index/page-index.js
index c8b79a8e57..0089bc7348 100644
--- a/use-timescale/page-index/page-index.js
+++ b/use-timescale/page-index/page-index.js
@@ -788,6 +788,11 @@ module.exports = [
href: "amazon-sagemaker",
excerpt: "Integrate Amazon SageMaker with Timescale Cloud",
},
+ {
+ title: "Amazon Web Services",
+ href: "aws",
+ excerpt: "Integrate AWS with Timescale Cloud",
+ },
{
title: "Apache Airflow",
href: "apache-airflow",
@@ -808,6 +813,11 @@ module.exports = [
href: "azure-data-studio",
excerpt: "Integrate Azure Data Studio with Timescale Cloud",
},
+ {
+ title: "Corporate data center",
+ href: "corporate-data-center",
+ excerpt: "Integrate your corporate data center with Timescale Cloud",
+ },
{
title: "Datadog",
href: "datadog",
@@ -828,11 +838,21 @@ module.exports = [
href: "fivetran",
excerpt: "Integrate Fivetran with Timescale Cloud",
},
+ {
+ title: "Google Cloud",
+ href: "google-cloud",
+ excerpt: "Integrate Google Cloud with Timescale Cloud",
+ },
{
title: "Grafana",
href: "grafana",
excerpt: "Integrate Grafana with Timescale products",
},
+ {
+ title: "Microsoft Azure",
+ href: "microsoft-azure",
+ excerpt: "Integrate Microsoft Azure with Timescale Cloud",
+ },
{
title: "pgAdmin",
href: "pgadmin",
diff --git a/use-timescale/security/transit-gateway.md b/use-timescale/security/transit-gateway.md
index 2a58786037..623f55da1b 100644
--- a/use-timescale/security/transit-gateway.md
+++ b/use-timescale/security/transit-gateway.md
@@ -9,85 +9,72 @@ cloud_ui:
- [services, :serviceId, operations, vpc]
---
+import TransitGatewayAWS from "versionContent/_partials/_transit-gateway-aws.mdx";
+import TransitGatewayOthers from "versionContent/_partials/_transit-gateway-others.mdx";
+
# Securely connect to $CLOUD_LONG from any cloud or on-premise environment
-[AWS Transit Gateway][aws-transit-gateway] enables you to securely connect to your $CLOUD_LONG from AWS, GCP, Azure, or any other cloud or on-premise environment.
+[AWS Transit Gateway][aws-transit-gateway] enables you to securely connect to your $CLOUD_LONG from AWS, Google Cloud, Microsoft Azure, or any other cloud or on-premise environment.
-You use AWS Transit Gateway as a traffic controller for your network. Instead of setting up multiple direct connections to different clouds, on-premise data centers, and other AWS services, you connect everything to Transit Gateway. This simplifies your network and makes it easier to manage and scale.
+You use AWS Transit Gateway as a traffic controller for your network. Instead of setting up multiple direct connections to different clouds, on-premise data centers, and other AWS services, you connect everything to AWS Transit Gateway. This simplifies your network and makes it easier to manage and scale.
You can then create a peering connection between your $SERVICE_LONGs and AWS Transit Gateway in $CLOUD_LONG. This means that, no matter how big or complex your infrastructure is, you can connect securely to your $SERVICE_LONGs.
To configure this secure connection, you:
-1. Create a $CLOUD_LONG Peering $VPC with a peering connection to your AWS Transit Gateway.
+1. Connect your infrastructure to AWS Transit Gateway.
+1. Create a $CLOUD_LONG Peering $VPC with a peering connection to AWS Transit Gateway.
1. Accept and configure the peering connection on your side.
1. Attach individual $SERVICE_SHORTs to the Peering $VPC.
-Transit Gateway feature is available for Scale and Enterprise [pricing plans][pricing-plans].
-
-## Create a Peering $VPC
-
-To create a Peering $VPC:
-
-
-
-1. **In [$CONSOLE][console-login] > `Security` > `VPC`, click `Create a VPC`**
-
- 
-
-1. **Choose your region and IP range, name your VPC, then click `Create VPC`**
+The AWS Transit Gateway feature is available for Scale and Enterprise [pricing plans][pricing-plans].
- 
+AWS Transit Gateway enable you to connect from almost any environment, this page provides examples for the most common use cases.
- Your $SERVICE_SHORT and Peering $VPC must be in the same AWS region. The number of Peering $VPCs you can create in your project depends on your [pricing plan][pricing-plans]. If you need another Peering $VPC, either contact [support@timescale.com](mailto:support@timescale.com) or change your pricing plan in [$CONSOLE][console-login].
+
-1. **Add a peering connection**
+
- 1. In the `VPC Peering` column, click `Add`.
- 1. Provide your AWS account ID, VPC ID or Transit Gateway ID, CIDR ranges, and AWS region.
- 1. Click `Add connection`.
+
- 
+
-
+
-## Accept and configure peering connection
+1. **Connect your infrastructure to AWS Transit Gateway**
-Once your peering connection appears as `Processing`, you can accept and configure it in AWS:
+ Establish connectivity between Azure and AWS. See the [AWS architectural documentation][azure-aws] for details.
-
+
-1. **Accept the peering request**
+
- In your AWS account, accept the peering request coming from $CLOUD_LONG. The request can take up to 5 min to arrive. Within 5 more minutes after accepting, the peering should appear as `Connected` in $CONSOLE.
+
-1. **Configure networking in your AWS account**
+1. **Connect your infrastructure to AWS Transit Gateway**
- Configure at least the following:
+ Establish connectivity between Google Cloud and AWS. See [Connect HA VPN to AWS peer gateways][gcp-aws].
- 1. Your subnet route table to route traffic to your Transit Gateway for the Peering VPC CIDRs.
- 1. Your Transit Gateway route table to route traffic to the newly created Transit Gateway peering attachment for the Peering VPC CIDRs.
- 1. Security groups to allow outbound TCP 5432.
+
-
+
-## Attach a $CLOUD_LONG service to the Peering VPC
+
-To attach a $SERVICE_SHORT to the Peering VPC:
+1. **Connect your infrastructure to AWS Transit Gateway**
-
+ Establish connectivity between your on-premise infrastructure and AWS. See the [Centralize network connectivity using AWS Transit Gateway][aws-onprem].
-1. **In [$CONSOLE][console-services], select the $SERVICE_SHORT you want to connect to the Peering VPC**
-1. **Click `Operations` > `Security` > `VPC`**
-1. **Select the VPC, then click `Attach VPC`**
+
- You cannot attach a $SERVICE_LONG to multiple $CLOUD_LONG $VPCs at the same time.
+
-
+
-You can now securely access your $SERVICE_SHORTs from any private cloud or on-premise data center connected to AWS Transit Gateway.
+You can now securely access your $SERVICE_SHORTs in $CLOUD_LONG.
[aws-transit-gateway]: https://aws.amazon.com/transit-gateway/
[pricing-plans]: /about/:currentVersion:/pricing-and-account-management/
-[console-login]: https://console.cloud.timescale.com/
-[console-services]: https://console.cloud.timescale.com/dashboard/services
\ No newline at end of file
+[azure-aws]: https://aws.amazon.com/blogs/modernizing-with-aws/designing-private-network-connectivity-aws-azure/
+[gcp-aws]: https://cloud.google.com/network-connectivity/docs/vpn/how-to/connect-ha-vpn-aws-peer-gateway
+[aws-onprem]: https://docs.aws.amazon.com/prescriptive-guidance/latest/patterns/centralize-network-connectivity-using-aws-transit-gateway.html