diff --git a/about/pricing-and-account-management.md b/about/pricing-and-account-management.md
index 79025ee6a0..8f537fa0ae 100644
--- a/about/pricing-and-account-management.md
+++ b/about/pricing-and-account-management.md
@@ -160,6 +160,7 @@ The features included in each [$PRICING_PLAN][pricing-plans] are:
| Performance insights | ✓ | ✓ | ✓ |
| Metrics and log exporters | | ✓ | ✓ |
| **Security and compliance** | | | |
+| Role-based access | ✓ | ✓ | ✓ |
| End-to-end encryption | ✓ | ✓ | ✓ |
| Private Networking (VPC) | 1 multi-attach VPC | Unlimited multi-attach VPCs | Unlimited multi-attach VPCs |
| AWS Transit Gateway | | ✓ | ✓ |
diff --git a/getting-started/run-queries-from-console.md b/getting-started/run-queries-from-console.md
index 48aafbd244..3532c3a47a 100644
--- a/getting-started/run-queries-from-console.md
+++ b/getting-started/run-queries-from-console.md
@@ -258,7 +258,7 @@ To use $SQL_EDITOR:
[portal-data-mode]: https://console.cloud.timescale.com/dashboard/services?popsql
[portal-ops-mode]: https://console.cloud.timescale.com/dashboard/services
[pricing-plan-features]: https://www.timescale.com/pricing#features
-[project-members]: /use-timescale/:currentVersion:/members/
+[project-members]: /use-timescale/:currentVersion:/security/members/
[query-variables]: https://docs.popsql.com/docs/query-variables
[read-replica]: /use-timescale/:currentVersion:/ha-replicas/read-scaling/
[run-popsql]: /getting-started/:currentVersion:/run-queries-from-console/#data-mode
diff --git a/integrations/cloudwatch.md b/integrations/cloudwatch.md
index e33ed768db..ba0b58a60e 100644
--- a/integrations/cloudwatch.md
+++ b/integrations/cloudwatch.md
@@ -33,7 +33,7 @@ tool. You create an exporter on the [project level][projects], in the same AWS r
-[projects]: /use-timescale/:currentVersion:/members/
+[projects]: /use-timescale/:currentVersion:/security/members/
[pricing-plan-features]: /about/:currentVersion:/pricing-and-account-management/#features-included-in-each-plan
[cloudwatch]: https://aws.amazon.com/cloudwatch/
[cloudwatch-signup]: https://docs.aws.amazon.com/AmazonCloudWatch/latest/monitoring/GettingSetup.html
diff --git a/integrations/datadog.md b/integrations/datadog.md
index 0765975c5f..964795d700 100644
--- a/integrations/datadog.md
+++ b/integrations/datadog.md
@@ -141,7 +141,7 @@ comprehensive list of [metrics][datadog-postgres-metrics] collected.
[datadog-monitor-cloud]: /integrations/:currentVersion:/datadog/#monitor-timescale-cloud-service-metrics-with-datadog
[datadog-agent]: /integrations/:currentVersion:/datadog/#configure-datadog-agent-to-collect-metrics-for-your-timescale-cloud-services
[datadog-agent-restart]: https://docs.datadoghq.com/agent/configuration/agent-commands/#start-stop-and-restart-the-agent
-[projects]: /use-timescale/:currentVersion:/members/
+[projects]: /use-timescale/:currentVersion:/security/members/
[datadog-api-key]: https://docs.datadoghq.com/account_management/api-app-keys/#add-an-api-key-or-client-token
[pricing-plan-features]: /about/:currentVersion:/pricing-and-account-management/#features-included-in-each-plan
[run-queries]: /getting-started/:currentVersion:/run-queries-from-console/
diff --git a/lambda/redirects.js b/lambda/redirects.js
index 0ec5952069..9aaf7b44c8 100644
--- a/lambda/redirects.js
+++ b/lambda/redirects.js
@@ -1053,4 +1053,8 @@ module.exports = [
from: '/use-timescale/latest/metrics-logging/insights/',
to: 'https://docs.tigerdata.com/use-timescale/latest/metrics-logging/monitoring/#insights',
}
+ {
+ from: '/use-timescale/latest/members/',
+ to: 'https://docs.tigerdata.com/use-timescale/latest/security/members/',
+ }
];
diff --git a/use-timescale/members.md b/use-timescale/members.md
deleted file mode 100644
index e3f4eb44b0..0000000000
--- a/use-timescale/members.md
+++ /dev/null
@@ -1,159 +0,0 @@
----
-title: User management
-excerpt: Manage your projects in Tiger Cloud Console. Add and delete users, join and leave projects, transfer project ownership, and configure authentication
-products: [cloud]
-keywords: [members, projects, admin, roles]
-tags: [users]
-cloud_ui:
- path:
- - [members]
----
-
-# Control user access to $PROJECT_LONGs
-
-When you sign up for a [30-day free trial][sign-up], $CLOUD_LONG creates a $PROJECT_SHORT for you, and
-you are assigned the `Owner` role for the $PROJECT_SHORT. As the $PROJECT_SHORT owner, you have rights to
-add and delete other users, and edit $PROJECT_SHORT settings. Users that you add to the $PROJECT_SHORT are
-assigned the `Member` role. Members have rights to collaborate with you on your $PROJECT_SHORT, and help
-create and administer the $SERVICE_SHORTs running in the $PROJECT_SHORT.
-
-
-
-If you have the [Enterprise pricing plan][pricing-plans], you can use your company [SAML][saml]
-identity provider to log in to $CONSOLE.
-
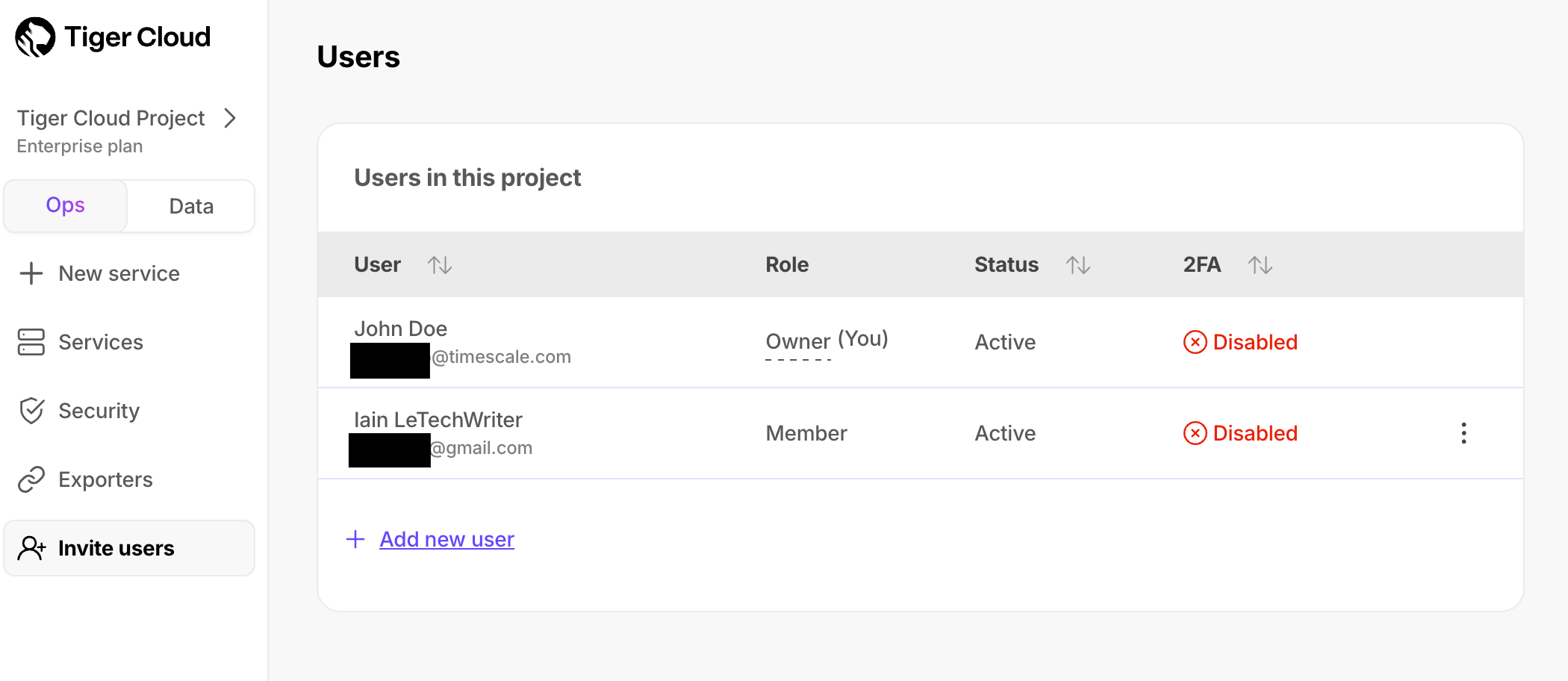
-## Add a user to your $PROJECT_SHORT
-
-New users do not need to have a $ACCOUNT_LONG before you add them, they are
-prompted to create one when they respond to the confirmation email. Existing users
-join a $PROJECT_SHORT in addition to the other $PROJECT_SHORTs they are already members of.
-
-To add a user to a $PROJECT_SHORT:
-
-
-
-1. In [$CONSOLE][cloud-login], click `Invite users`, then click `Add new user`.
- 
-
-1. Type the email address of the person that you want to add, and click `Add
- user`.
-
- [Enterprise plan][pricing-plans] and SAML users receive a notification in $CONSOLE. Users in the
- other pricing plans receive a confirmation email. The new user then [joins the $PROJECT_SHORT][join-a-project].
-
-
-
-## Join a $PROJECT_SHORT
-
-When you are asked to join a $PROJECT_SHORT, the $CONSOLE sends you an invitation email. Follow the
-instructions in the invitation email to join the $PROJECT_SHORT:
-
-- **New $CLOUD_LONG user**:
- 1. In the invitation email, click **Accept Invite**.
- $CLOUD_LONG opens.
- 2. Follow the setup wizard and create a new $ACCOUNT_SHORT.
-
- You are added to the $PROJECT_SHORT you were invited to.
-
-- **Existing $CLOUD_LONG user**:
- 1. In the invitation email, click **Accept Invite**.
-
- $CONSOLE_LONG opens and you are added to the $PROJECT_SHORT.
-
-- **[Enterprise plan][pricing-plans] and SAML user**:
- 1. Log in to $CONSOLE_SHORT using your company's identity provider.
- 2. Click `Notifications`, then accept the invitation.
-
- $CONSOLE_LONG opens, and you are added to the $PROJECT_SHORT. As you are now
- included in more than one $PROJECT_SHORT, you can easily [change $PROJECT_SHORTs][change-project].
-
-
-## Resend a $PROJECT_SHORT invitation
-
-$PROJECT_SHORT_CAP invitations are valid for 7 days. To resend a $PROJECT_SHORT invitation:
-
-
-
-1. In [$CONSOLE][cloud-login], click `Invite users`.
- 
-1. Next to the person you want to invite to your $PROJECT_SHORT, click `Resend invitation`.
-
-
-
-## Change the current $PROJECT_SHORT
-
-To change the $PROJECT_SHORT you are currently working in:
-
-
-
-1. In [$CONSOLE][cloud-login], click `Tiger Cloud Project`, then `Current project`.
- 
-2. Select the $PROJECT_SHORT you want to use.
-
-You can now manage the users and $SERVICE_SHORTs in this $PROJECT_SHORT.
-
-
-
-## Transfer $PROJECT_SHORT ownership
-
-Each $PROJECT_SHORT in $CONSOLE has one `owner`. As the $PROJECT_SHORT owner, you have rights to
-add and delete users, edit $PROJECT_SHORT settings, and transfer the owner role to another user. When you transfer
-ownership to another user, you lose your ownership rights.
-
-To transfer $PROJECT_SHORT ownership:
-
-
-
-1. In [$CONSOLE][cloud-login], click `Invite users`.
-2. Next to the person you want to transfer project ownership to, click `⋮` > `Transfer project ownership`.
- 
- If you are unable to transfer ownership, hover over the greyed out button to see the details.
-3. Enter your password, and click `Verify`.
-4. Complete the two-factor authentication challenge and click `Confirm`.
-
-
-
-If you have the [Enterprise pricing plan][pricing-plans], and log in to $CLOUD_LONG using [SAML authentication][saml]
-or have not enabled [two-factor authentication][2fa], [contact support](https://www.timescale.com/contact) to transfer
-$PROJECT_SHORT ownership.
-
-
-## Leave a $PROJECT_SHORT
-
-To stop working in a $PROJECT_SHORT:
-
-
-
-1. In [$CONSOLE][cloud-login], click `Invite users`.
-1. Click `⋮` > `Leave project`, then click `Leave`.
- 
-
-Your $ACCOUNT_SHORT is removed from the $PROJECT_SHORT immediately, you can no longer access this $PROJECT_SHORT.
-
-
-
-## Remove users from a $PROJECT_SHORT
-
-To remove a user's access to a $PROJECT_SHORT:
-
-
-
-1. In [$CONSOLE][cloud-login], click `Invite users`.
-1. Next to the person you want to remove, click `⋮` > `Remove`.
- 
-1. In `Remove user`, click `Remove`.
-
-The user is deleted immediately, they can no longer access your $PROJECT_SHORT.
-
-
-
-
-[cloud-login]: https://console.cloud.timescale.com/
-[saml]: /use-timescale/:currentVersion:/security/saml/
-[2fa]: /use-timescale/:currentVersion:/security/multi-factor-authentication/
-[cloud-login]: https://console.cloud.timescale.com/
-[sign-up]: https://console.cloud.timescale.com/
-[pricing-plans]: /about/:currentVersion:/pricing-and-account-management/
-[join-a-project]: /use-timescale/:currentVersion:/members/#join-a-project
-[change-project]: /use-timescale/:currentVersion:/members/#change-the-current-project
-[saml]: https://en.wikipedia.org/wiki/SAML_2.0
\ No newline at end of file
diff --git a/use-timescale/metrics-logging/aws-cloudwatch.md b/use-timescale/metrics-logging/aws-cloudwatch.md
index a4b4588c47..6c155ee5fe 100644
--- a/use-timescale/metrics-logging/aws-cloudwatch.md
+++ b/use-timescale/metrics-logging/aws-cloudwatch.md
@@ -41,4 +41,4 @@ This section shows you how to attach, monitor, edit, and delete a data exporter.
[console-services]: https://console.cloud.timescale.com/dashboard/services
[services-portal]: https://console.cloud.timescale.com/dashboard/services
[pricing-plan-features]: /about/:currentVersion:/pricing-and-account-management/#features-included-in-each-plan
-[projects]: /use-timescale/:currentVersion:/members/
\ No newline at end of file
+[projects]: /use-timescale/:currentVersion:/security/members/
\ No newline at end of file
diff --git a/use-timescale/metrics-logging/datadog.md b/use-timescale/metrics-logging/datadog.md
index 511c8f6483..431551cfee 100644
--- a/use-timescale/metrics-logging/datadog.md
+++ b/use-timescale/metrics-logging/datadog.md
@@ -42,4 +42,4 @@ This section shows you how to attach, monitor, edit, and delete a data exporter.
[console-services]: https://console.cloud.timescale.com/dashboard/services
[services-portal]: https://console.cloud.timescale.com/dashboard/services
[pricing-plan-features]: /about/:currentVersion:/pricing-and-account-management/#features-included-in-each-plan
-[projects]: /use-timescale/:currentVersion:/members/
+[projects]: /use-timescale/:currentVersion:/security/members/
diff --git a/use-timescale/page-index/page-index.js b/use-timescale/page-index/page-index.js
index 56dd340835..17e7974918 100644
--- a/use-timescale/page-index/page-index.js
+++ b/use-timescale/page-index/page-index.js
@@ -173,11 +173,6 @@ module.exports = [
},
],
},
- {
- title: "Control user access to Tiger Cloud projects",
- href: "members",
- excerpt: "User management in Tiger Cloud",
- },
{
title: "Write data",
href: "write-data",
@@ -701,6 +696,16 @@ module.exports = [
href: "overview",
excerpt: "Get an overview of Tiger Cloud security",
},
+ {
+ title: "Control user access to projects",
+ href: "members",
+ excerpt: "Project and user role management in Tiger Cloud",
+ },
+ {
+ title: "Manage data security in your service",
+ href: "read-only-role",
+ excerpt: "Restrict access to your data with roles",
+ },
{
title: "SAML authentication",
href: "saml",
@@ -717,11 +722,6 @@ module.exports = [
excerpt:
"Client credentials to programmatically access your Tiger Cloud account",
},
- {
- title: "Read only role",
- href: "read-only-role",
- excerpt: "Create a read-only role to access your database",
- },
{
title: "Connect with a stricter SSL mode",
href: "strict-ssl",
diff --git a/use-timescale/security/index.md b/use-timescale/security/index.md
index 25bc25b8f2..e3b07bfd82 100644
--- a/use-timescale/security/index.md
+++ b/use-timescale/security/index.md
@@ -7,13 +7,13 @@ keywords: [security]
# Security
-Learn how your $SERVICE_LONG is secured to protect your data and
-privacy.
+Learn how $CLOUD_LONG protects your data and privacy.
* Learn about [security in $CLOUD_LONG][overview]
+* Restrict access to your [$PROJECT_SHORT][console-rbac]
+* Restrict access to the [data in your $SERVICE_SHORT][read-only]
* Set up [multifactor][mfa] and [SAML][saml] authentication
* Generate multiple [client credentials][client-credentials] instead of using your username and password
-* Grant [read-only access][read-only] to your data
* Connect with a [stricter SSL mode][ssl]
* Secure your $SERVICE_SHORTs with [VPC peering][vpc-peering]
* Connect to your $SERVICE_SHORTs from any cloud with [AWS Transit Gateway][transit-gateway]
@@ -27,4 +27,5 @@ privacy.
[read-only]: /use-timescale/:currentVersion:/security/read-only-role/
[vpc-peering]: /use-timescale/:currentVersion:/security/vpc/
[ip-allowlist]: /use-timescale/:currentVersion:/security/ip-allow-list/
-[transit-gateway]: /use-timescale/:currentVersion:/security/transit-gateway/
\ No newline at end of file
+[transit-gateway]: /use-timescale/:currentVersion:/security/transit-gateway/
+[console-rbac]: /use-timescale/:currentVersion:/security/members/
\ No newline at end of file
diff --git a/use-timescale/security/ip-allow-list.md b/use-timescale/security/ip-allow-list.md
index 2f24cc514f..f10f32c6c3 100644
--- a/use-timescale/security/ip-allow-list.md
+++ b/use-timescale/security/ip-allow-list.md
@@ -75,7 +75,7 @@ You have successfully added an IP allow list for querying your $SERVICE_SHORT in
[console]: https://console.cloud.timescale.com/dashboard/
[pricing-plans]: /about/:currentVersion:/pricing-and-account-management/
[vpc-peering]: /use-timescale/:currentVersion:/security/vpc/
-[members]: /use-timescale/:currentVersion:/members/
+[members]: /use-timescale/:currentVersion:/security/members/
[modes]: /getting-started/:currentVersion:/services/
diff --git a/use-timescale/security/members.md b/use-timescale/security/members.md
new file mode 100644
index 0000000000..f20c81a777
--- /dev/null
+++ b/use-timescale/security/members.md
@@ -0,0 +1,217 @@
+---
+title: Control access to Tiger Cloud projects
+excerpt: Manage your projects and services in Tiger Cloud Console. Add and delete users, assign roles, join and leave projects, transfer project ownership, and configure authentication
+products: [cloud]
+keywords: [members, projects, admin, roles]
+tags: [users]
+cloud_ui:
+ path:
+ - [members]
+---
+
+# Control user access to Tiger Cloud projects
+
+When you sign up for a [30-day free trial][sign-up], $CLOUD_LONG creates a $PROJECT_SHORT with built-in role-based access. This includes the following roles:
+
+- **Owner**: $CLOUD_LONG assigns this role to you when your $PROJECT_SHORT is created. As the Owner, you can add and delete other users, transfer project ownership, administer $SERVICE_SHORTs, and edit $PROJECT_SHORT settings.
+- **Admin**: the Owner assigns this role to other users in the $PROJECT_SHORT. A user with the Admin role has the same scope of rights as the Owner but cannot transfer project ownership.
+- **Viewer**: the Owner and Admins assign this role to other users in the $PROJECT_SHORT. A Viewer has limited, read-only access to $CONSOLE_LONG. This means that a Viewer cannot modify $SERVICE_SHORTs and their configurations in any way. A Viewer has no access to the $DATA_MODE and has read-queries-only access to $SQL_EDITOR.
+
+
+
+If you have the [$ENTERPRISE $PRICING_PLAN][pricing-plans], you can use your company [SAML][saml]
+identity provider to log in to $CONSOLE_SHORT.
+
+
+
+User roles in a $PROJECT_LONG do not overlap with the database-level roles for the individual $SERVICE_SHORTs. This page describes the $PROJECT_SHORT roles available in $CONSOLE_SHORT. For the database-level user roles, see [Manage data security in your $SERVICE_LONG][database-rbac].
+
+
+
+## Add a user to your $PROJECT_SHORT
+
+New users do not need to have a $ACCOUNT_LONG before you add them, they are
+prompted to create one when they respond to the confirmation email. Existing users
+join a $PROJECT_SHORT in addition to the other $PROJECT_SHORTs they are already members of.
+
+To add a user to a $PROJECT_SHORT:
+
+
+
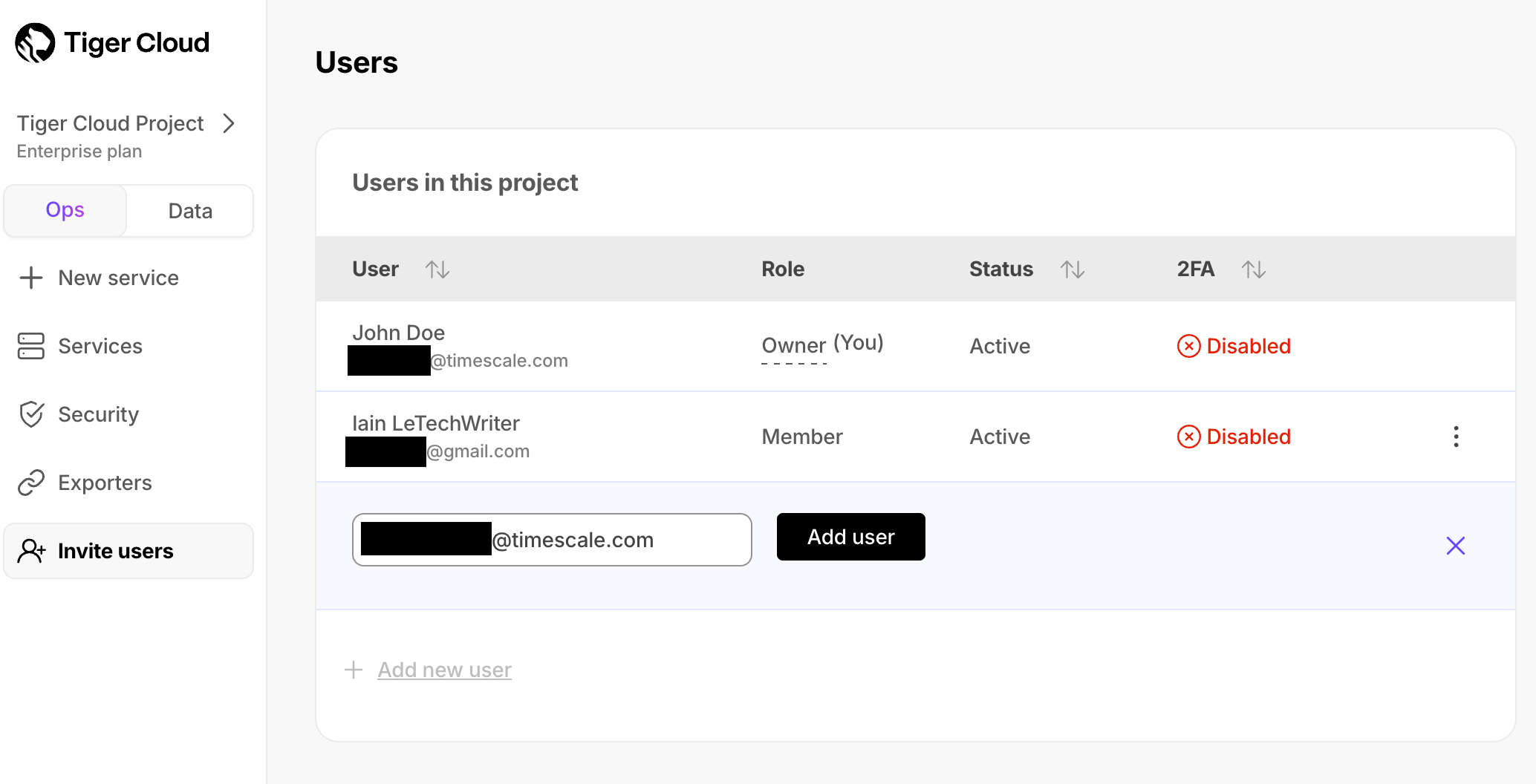
+1. In [$CONSOLE][cloud-login], click `Invite users`, then click `Add new user`.
+
+1. Type the email address of the person that you want to add, select their role, and click `Invite
+ user`.
+
+ 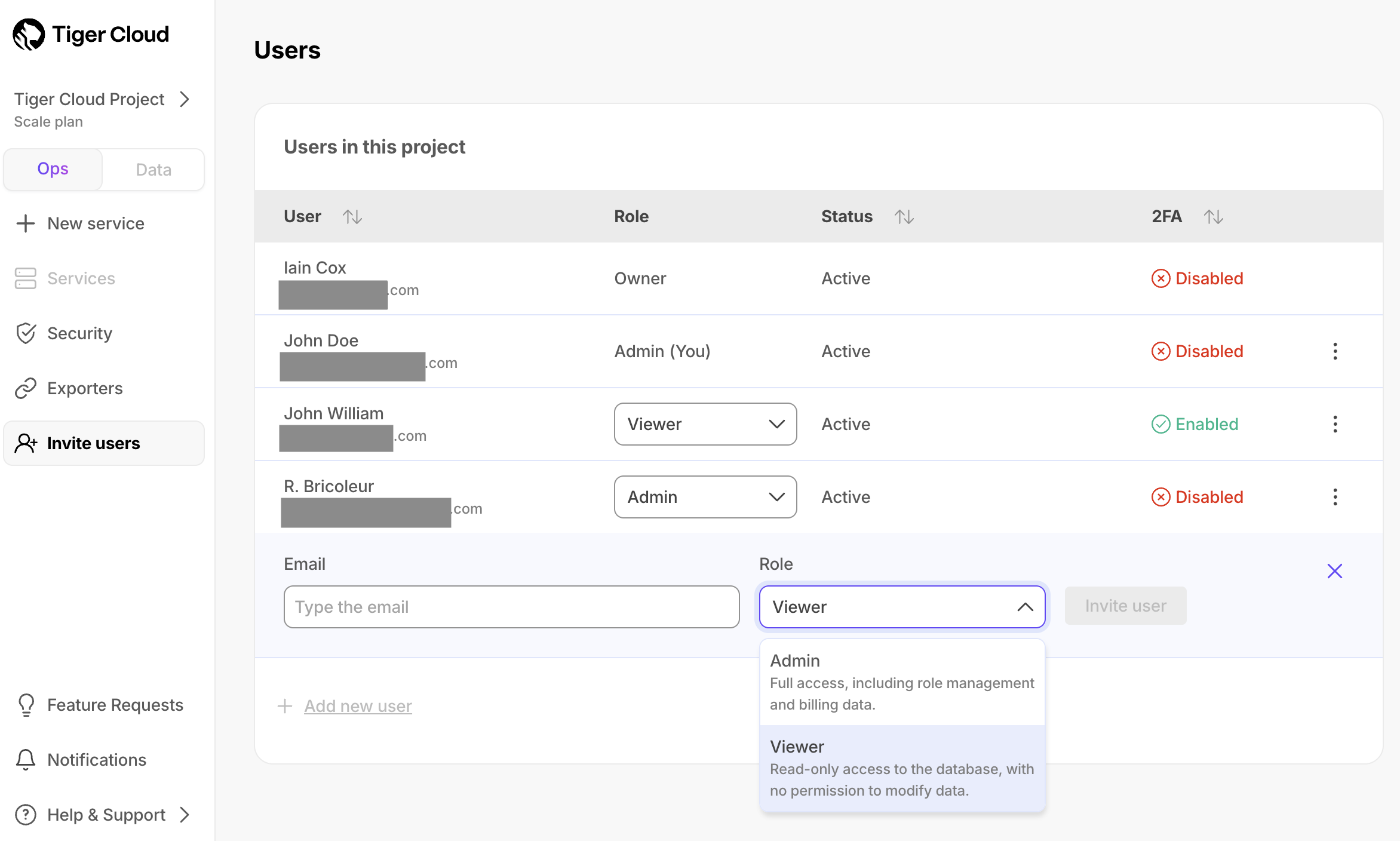
+
+ [$ENTERPRISE $PRICING_PLAN][pricing-plans] and SAML users receive a notification in $CONSOLE_SHORT. Users in the
+ other $PRICING_PLANs receive a confirmation email. The new user then [joins the $PROJECT_SHORT][join-a-project].
+
+
+
+## Join a $PROJECT_SHORT
+
+When you are asked to join a $PROJECT_SHORT, $CONSOLE sends you an invitation email. Follow the
+instructions in the invitation email to join the $PROJECT_SHORT:
+
+
+
+
+
+
+
+1. **In the invitation email, click `Accept Invite`**
+
+ $CLOUD_LONG opens.
+
+1. **Follow the setup wizard and create a new $ACCOUNT_SHORT**
+
+ You are added to the $PROJECT_SHORT you were invited to.
+
+
+
+
+
+
+
+
+
+1. **In the invitation email, click `Accept Invite`**
+
+ $CONSOLE_LONG opens, and you are added to the $PROJECT_SHORT.
+
+
+
+
+
+
+
+
+
+1. **Log in to $CONSOLE_SHORT using your company's identity provider**
+
+1. **Click `Notifications`, then accept the invitation**
+
+ $CONSOLE_LONG opens, and you are added to the $PROJECT_SHORT. As you are now included in more than one $PROJECT_SHORT, you can easily [change $PROJECT_SHORTs][change-project].
+
+
+
+
+
+
+
+## Resend a $PROJECT_SHORT invitation
+
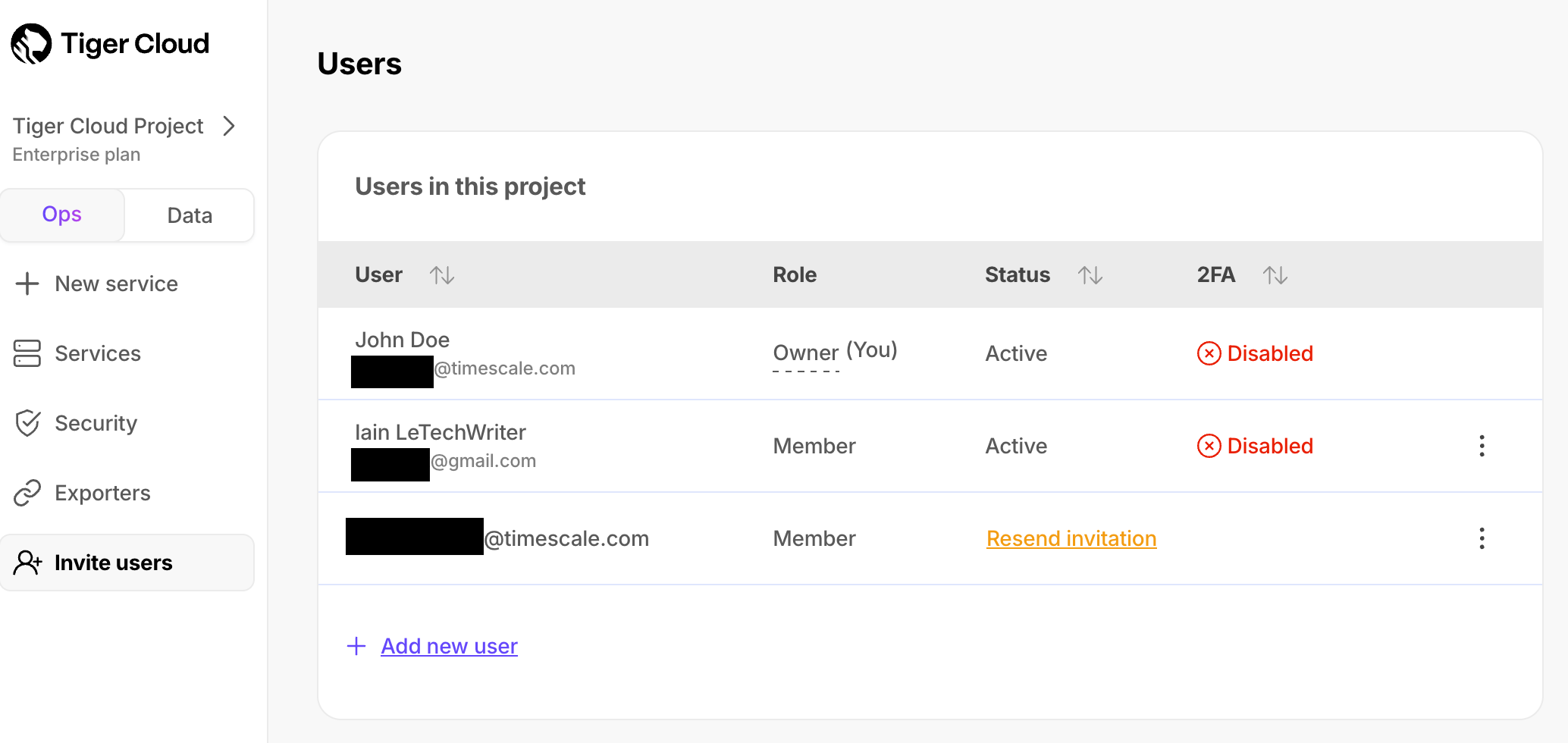
+$PROJECT_SHORT_CAP invitations are valid for 7 days. To resend a $PROJECT_SHORT invitation:
+
+
+
+1. In [$CONSOLE][cloud-login], click `Invite users`.
+
+1. Next to the person you want to invite to your $PROJECT_SHORT, click `Resend invitation`.
+
+ 
+
+
+
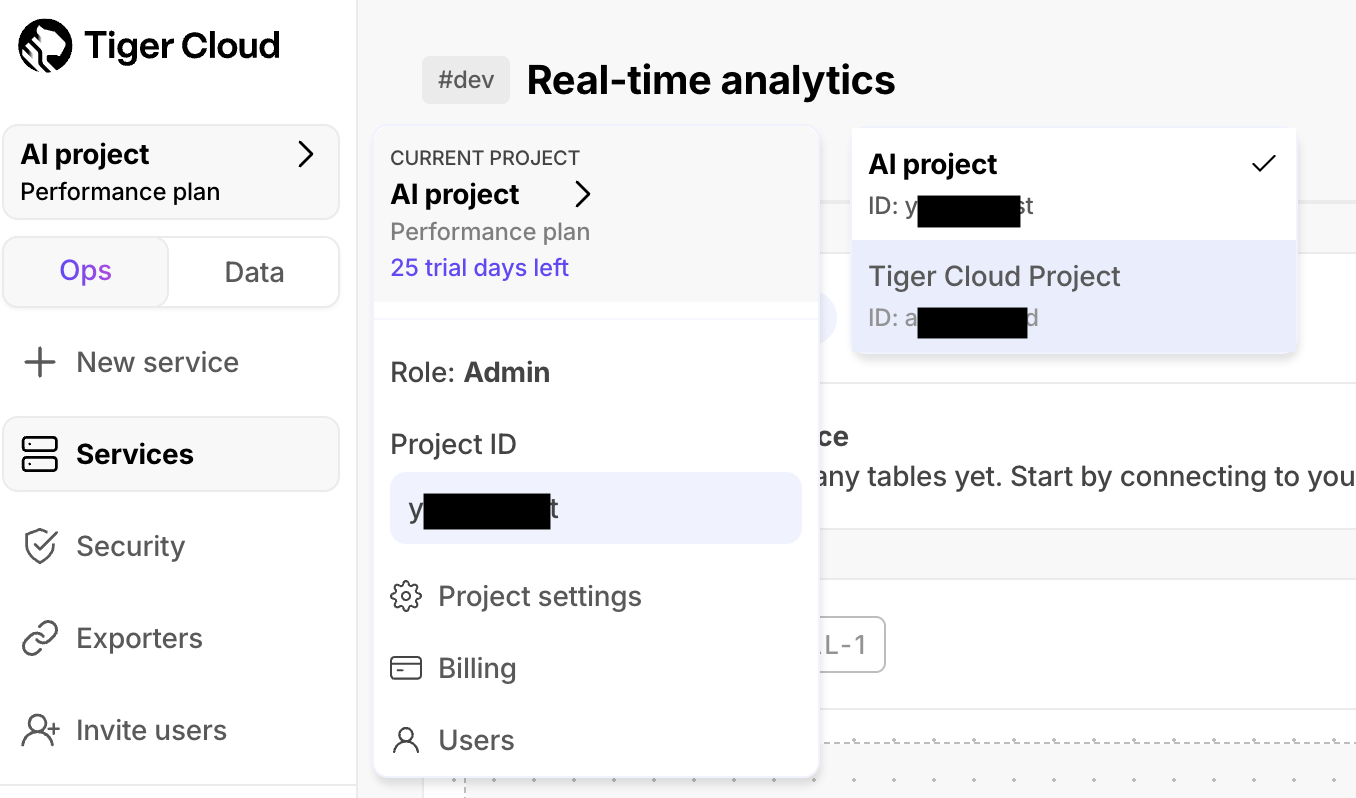
+## Change your current $PROJECT_SHORT
+
+To change the $PROJECT_SHORT you are currently working in:
+
+
+
+1. In [$CONSOLE][cloud-login], click the $PROJECT_SHORT name > `Current project` in the top left.
+
+ 
+
+1. Select the $PROJECT_SHORT you want to use.
+
+
+
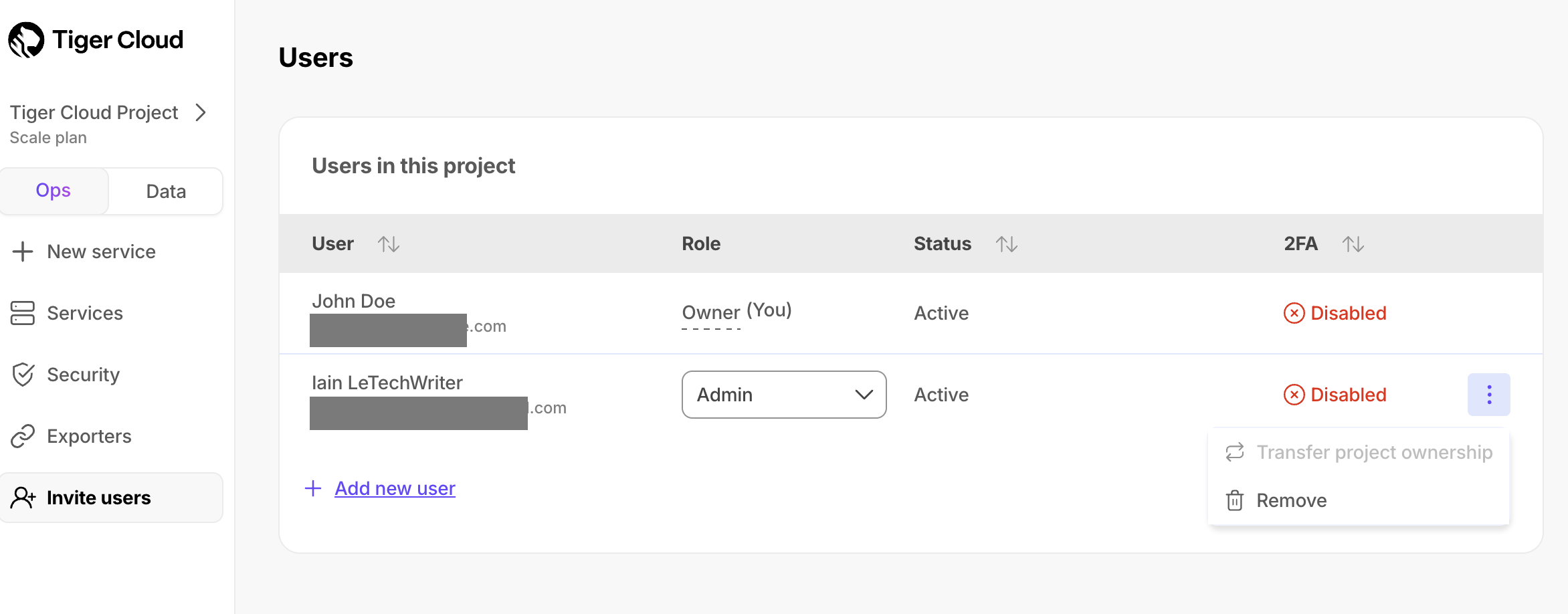
+## Transfer $PROJECT_SHORT ownership
+
+Each $PROJECT_LONG has one Owner. As the $PROJECT_SHORT Owner, you have rights to
+add and delete users, edit $PROJECT_SHORT settings, and transfer the Owner role to another user. When you transfer
+ownership to another user, you lose your ownership rights.
+
+To transfer $PROJECT_SHORT ownership:
+
+
+
+1. In [$CONSOLE][cloud-login], click `Invite users`.
+
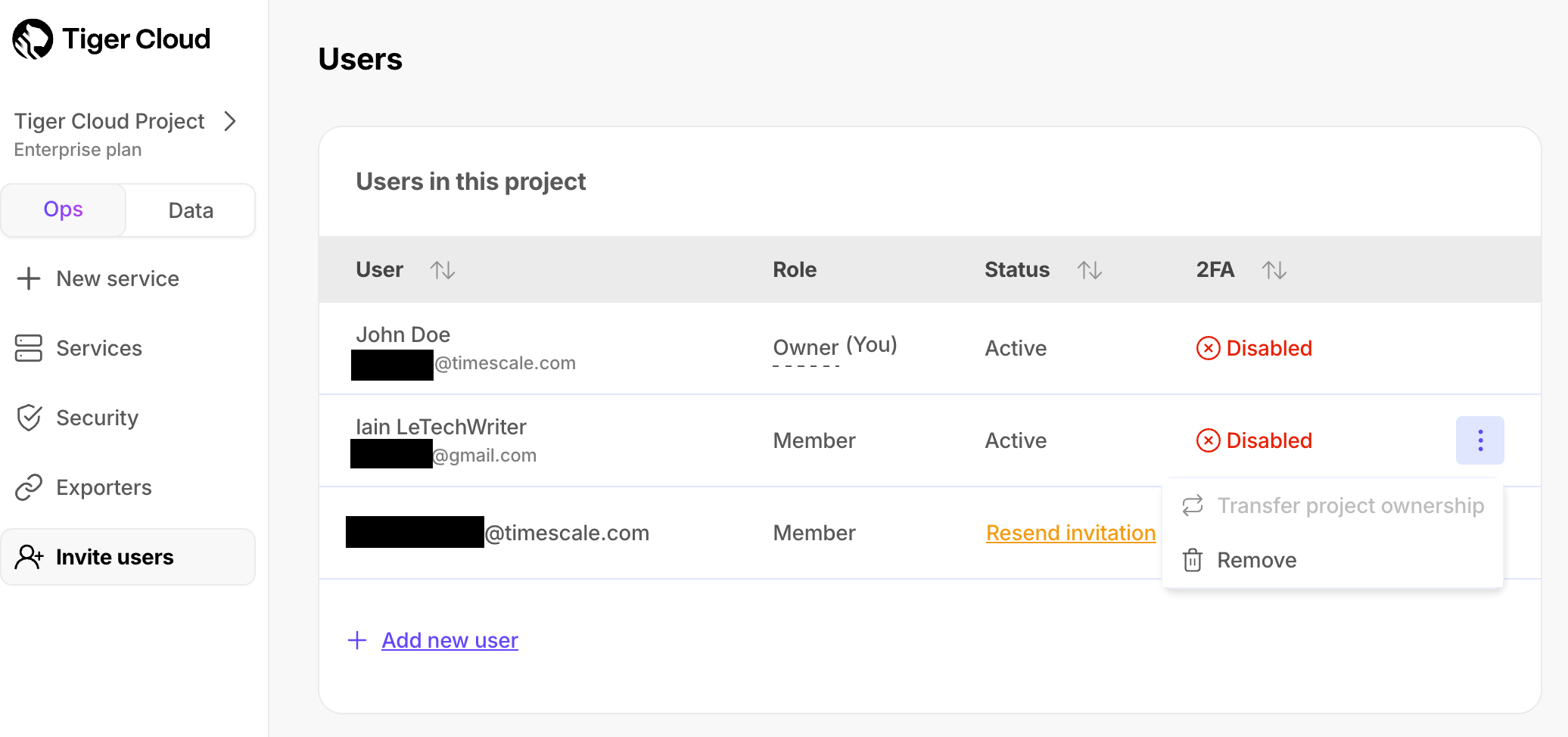
+1. Next to the person you want to transfer project ownership to, click `⋮` > `Transfer project ownership`.
+
+ 
+
+ If you are unable to transfer ownership, hover over the greyed out button to see the details.
+
+1. Enter your password, and click `Verify`.
+1. Complete the two-factor authentication challenge and click `Confirm`.
+
+
+
+If you have the [Enterprise pricing plan][pricing-plans], and log in to $CLOUD_LONG using [SAML authentication][saml]
+or have not enabled [two-factor authentication][2fa], [contact support](https://www.tigerdata.com/contact) to transfer
+$PROJECT_SHORT ownership.
+
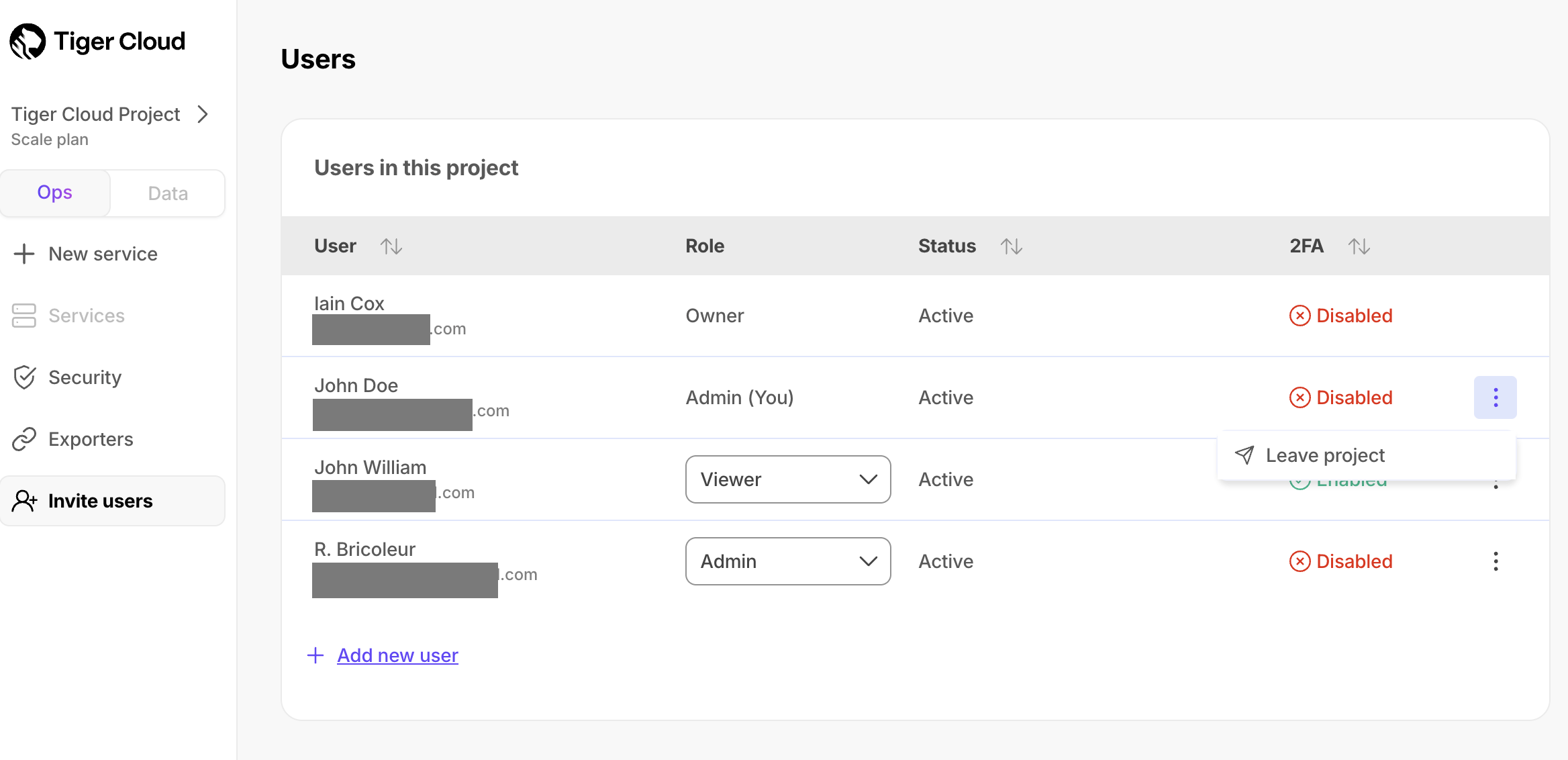
+## Leave a $PROJECT_SHORT
+
+To stop working in a $PROJECT_SHORT:
+
+
+
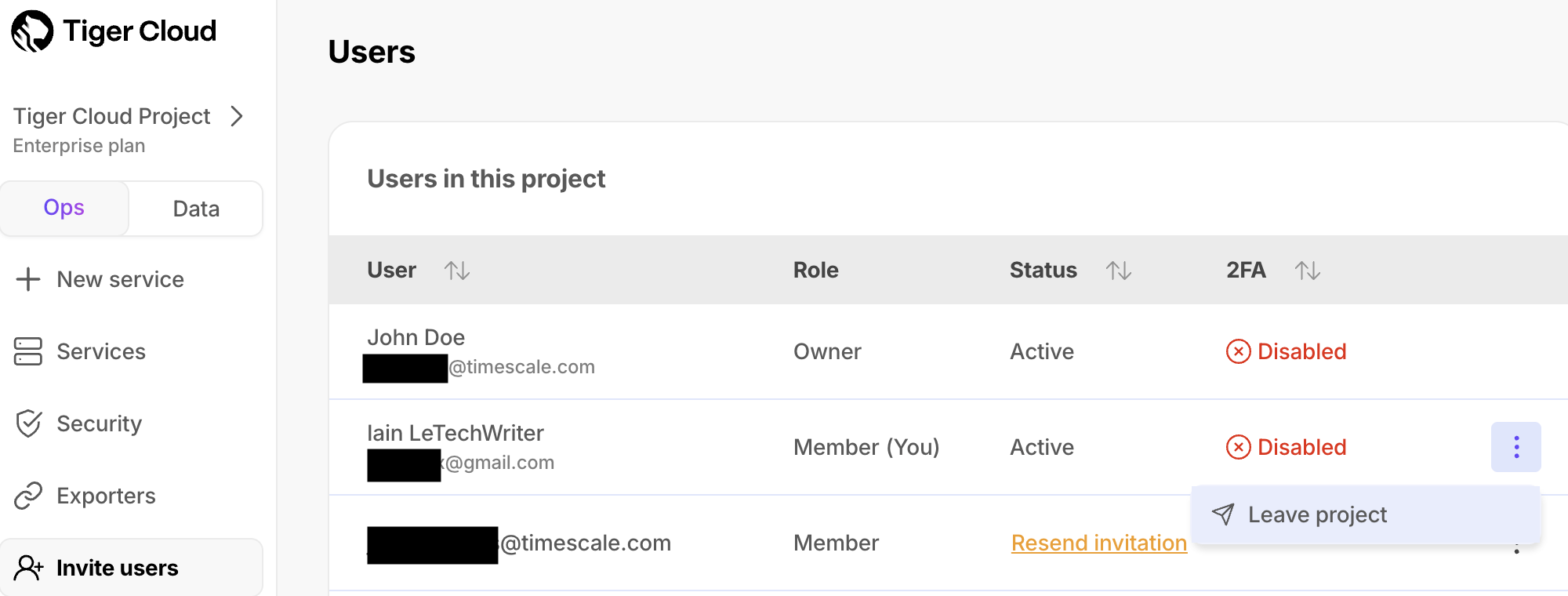
+1. In [$CONSOLE][cloud-login], click `Invite users`.
+
+1. Click `⋮` > `Leave project`, then click `Leave`.
+
+ 
+
+Your $ACCOUNT_SHORT is removed from the $PROJECT_SHORT immediately, you can no longer access this $PROJECT_SHORT.
+
+
+
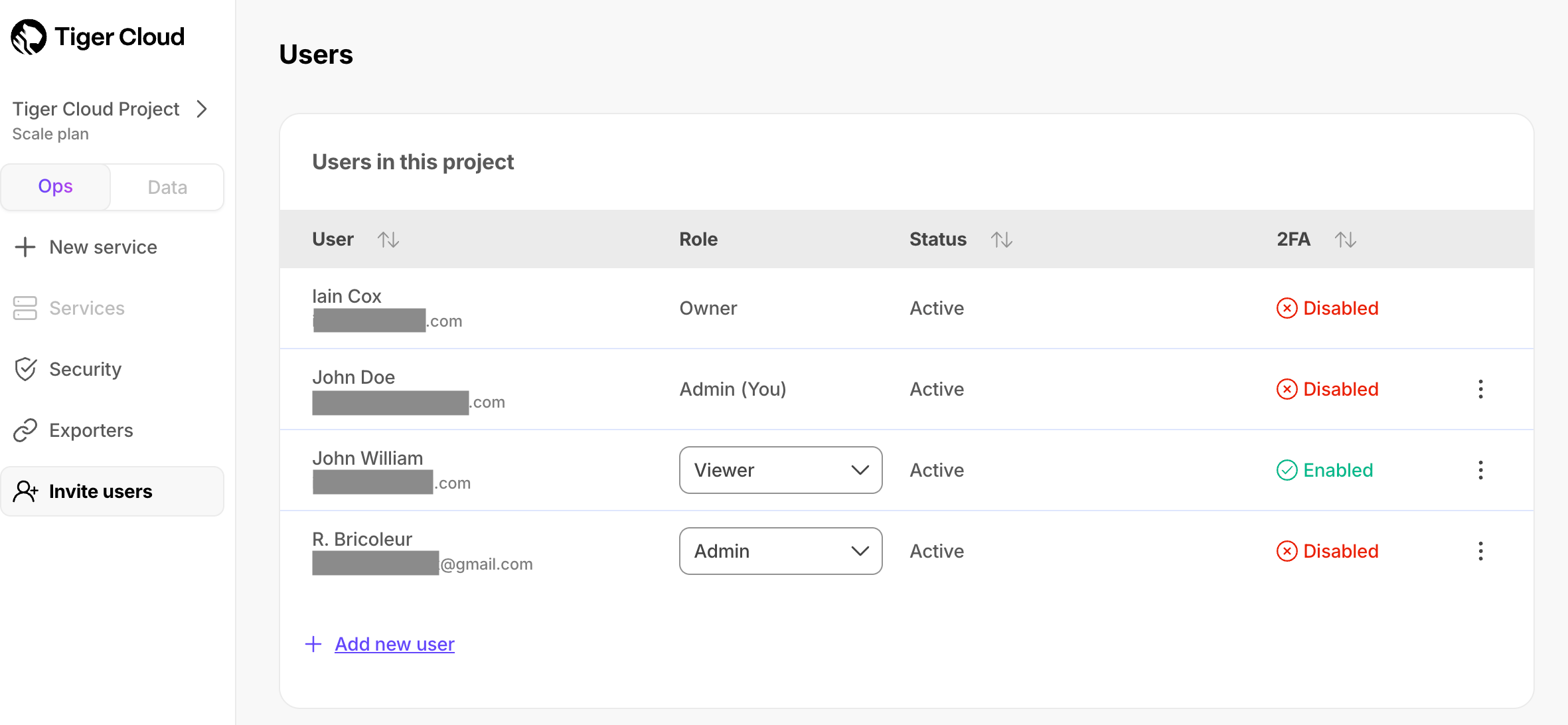
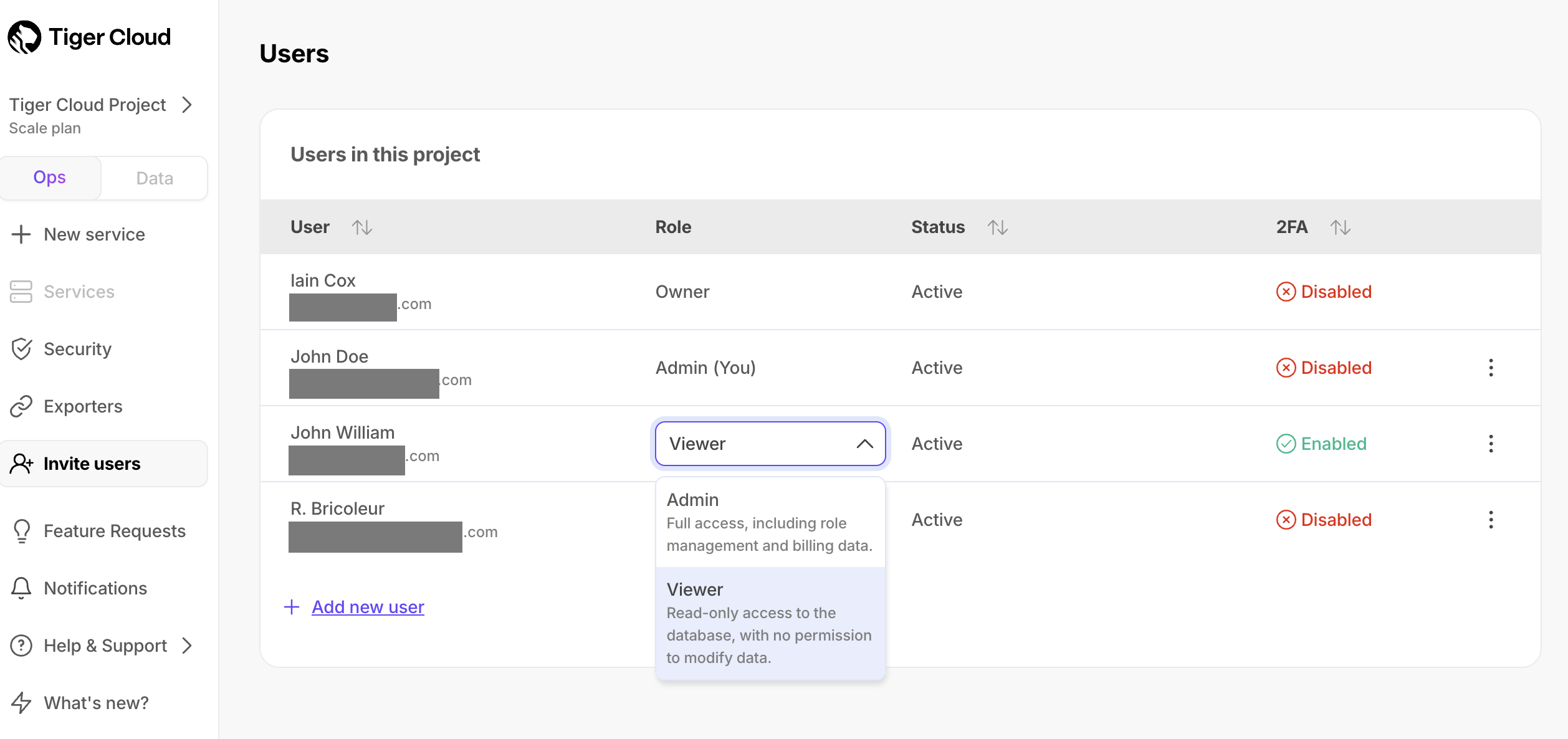
+## Change roles of other users in a $PROJECT_SHORT
+
+The Owner can change the roles of all users in the $PROJECT_SHORT. An Admin can change the roles of all users other than the Owner.
+
+To change the role for another user:
+
+
+
+1. In [$CONSOLE][cloud-login], click `Invite users`.
+
+1. Next to the corresponding user, select another role in the dropdown.
+
+ 
+
+ The user role is changed immediately.
+
+
+
+## Remove users from a $PROJECT_SHORT
+
+To remove a user's access to a $PROJECT_SHORT:
+
+
+
+1. In [$CONSOLE][cloud-login], click `Invite users`.
+1. Next to the person you want to remove, click `⋮` > `Remove`.
+ 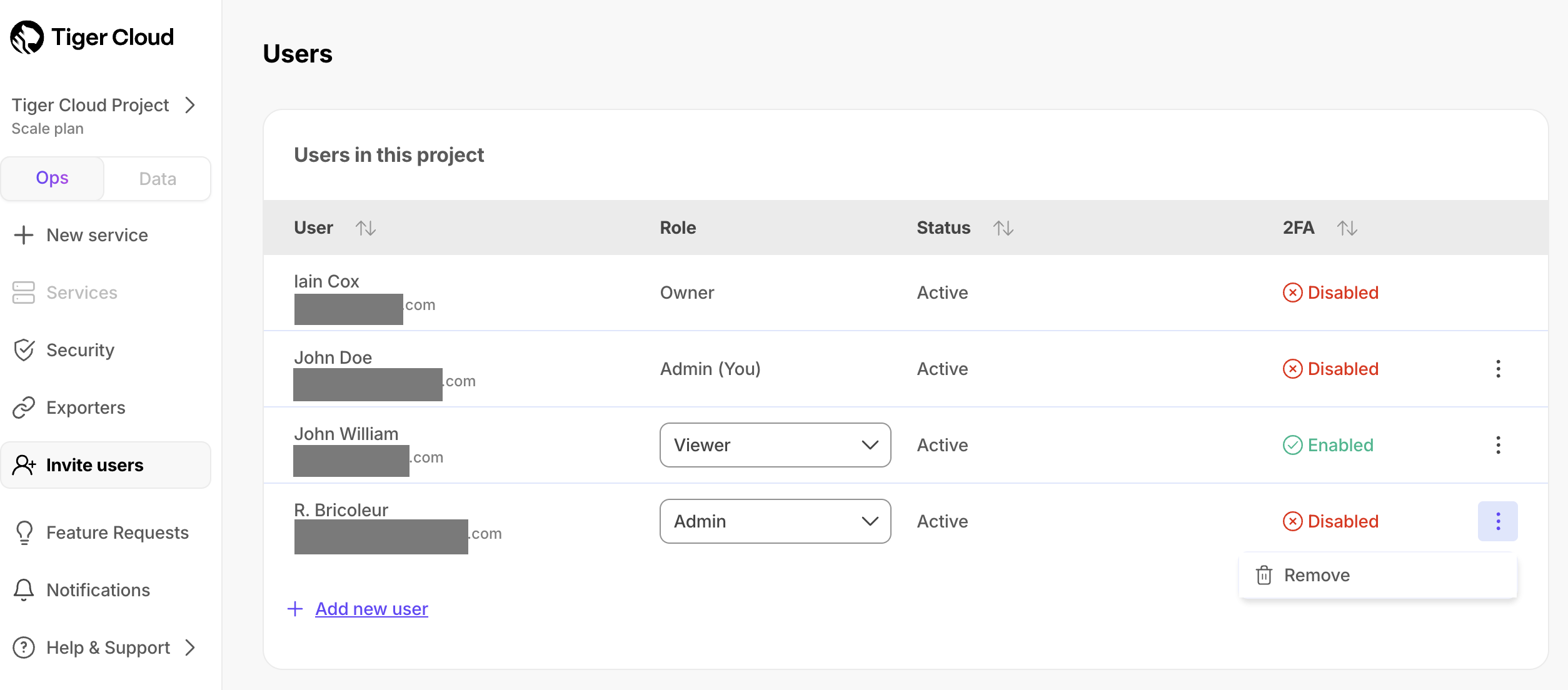
+1. In `Remove user`, click `Remove`.
+
+The user is deleted immediately, they can no longer access your $PROJECT_SHORT.
+
+
+
+
+[cloud-login]: https://console.cloud.timescale.com/
+[saml]: /use-timescale/:currentVersion:/security/saml/
+[2fa]: /use-timescale/:currentVersion:/security/multi-factor-authentication/
+[sign-up]: https://console.cloud.timescale.com/
+[pricing-plans]: /about/:currentVersion:/pricing-and-account-management/
+[join-a-project]: /use-timescale/:currentVersion:/security/members/#join-a-project
+[change-project]: /use-timescale/:currentVersion:/security/members/#change-the-current-project
+[saml]: https://en.wikipedia.org/wiki/SAML_2.0
+[database-rbac]: /use-timescale/:currentVersion:/security/read-only-role/
\ No newline at end of file
diff --git a/use-timescale/security/overview.md b/use-timescale/security/overview.md
index e353bbe0f8..8fea3090a6 100644
--- a/use-timescale/security/overview.md
+++ b/use-timescale/security/overview.md
@@ -17,6 +17,15 @@ $COMPANY products do not have any identified weaknesses.
This page lists the additional things we do to ensure operational security and to lock down $SERVICE_LONGs.
To see our security features at a glance, see [$COMPANY Security][security-at-timescale].
+## Role-based access
+
+$CLOUD_LONG provides role-based access for you to:
+
+* Administer your $PROJECT_LONG
+ In $CONSOLE_LONG, users with the Owner, Admin, and Viewer roles have different permissions to manage users and $SERVICE_SHORTs in the $PROJECT_SHORT.
+* Manage data in each $SERVICE_SHORT
+ To restrict access to your data on the database level, you can create other roles on top of the default tsdbadmin role.
+
## Data encryption
Your data on $CLOUD_LONG is encrypted both in transit and at rest. Both active
diff --git a/use-timescale/security/read-only-role.md b/use-timescale/security/read-only-role.md
index 2f395ab38f..e814d745e8 100644
--- a/use-timescale/security/read-only-role.md
+++ b/use-timescale/security/read-only-role.md
@@ -1,20 +1,20 @@
---
-title: Read-only role
-excerpt: Tiger Cloud includes different levels of access to your services and data for enhanced security. Learn how to grant read-only access to your data
+title: Manage data security in your Tiger Cloud service
+excerpt: Learn about the available user roles to access data in your database
products: [cloud]
keywords: [client credentials, accounts, users, members, read-only, security]
tags: [authentication, credentials, members, security]
---
-# Read-only user
+# Manage data security in your Tiger Cloud service
-You can create a role that provides read-only access to your database.
+When you create a $SERVICE_SHORT, $CLOUD_LONG assigns you the tsdmadmin role. This role has full permissions to modify data in your $SERVICE_SHORT. However, $CLOUD_LONG does not provide superuser access. tsdmadmin is not a superuser.
+
+As tsdmadmin, you can use standard $PG means to create other roles or assign individual permissions. This page shows you how to create a read-only role for your database. Adding a read-only role does not provide resource isolation. To restrict the access of a read-only user, as well as isolate resources, create a [read replica][read-scaling] instead.
-Adding a read-only user role to your database does not provide resource
-isolation. If you want to restrict the access of a read-only user, as well as isolate resources, you can create a read replica instead. For more information, see the
-[read scaling](/use-timescale/latest/ha-replicas/read-scaling/) section.
+The database-level roles for the individual $SERVICE_SHORTs in your $PROJECT_SHORT do not overlap with the $PROJECT_LONG user roles. This page describes the database-level roles. For user roles available in $CONSOLE_SHORT, see [Control user access to Tiger Cloud projects][console-rbac].
@@ -24,11 +24,9 @@ You can create a read-only user to provide limited access to your database.
-### Creating a read-only user
-
-1. Connect to your database as the `tsdbadmin` user.
+1. Connect to your $SERVICE_SHORT as the tsdbadmin user.
-1. At the psql prompt, create the new role:
+1. Create the new role:
```sql
CREATE ROLE readaccess;
@@ -60,3 +58,6 @@ You can create a read-only user to provide limited access to your database.
```
+
+[console-rbac]: /use-timescale/:currentVersion:/security/members/
+[read-scaling]: /use-timescale/:currentVersion:/ha-replicas/read-scaling/
diff --git a/use-timescale/security/vpc.md b/use-timescale/security/vpc.md
index f867e2b229..d3046b683f 100644
--- a/use-timescale/security/vpc.md
+++ b/use-timescale/security/vpc.md
@@ -228,4 +228,4 @@ some time for DNS propagation.
[aws-vpc-connect-vpcs]: /use-timescale/:currentVersion:/security/vpc/#attach-a-timescale-service-to-the-peering-vpc
[create-service]: /getting-started/:currentVersion:/services/#create-a-timescale-cloud-service
[pricing-plans]: /about/:currentVersion:/pricing-and-account-management/
-[project-members]: /use-timescale/:currentVersion:/members/
+[project-members]: /use-timescale/:currentVersion:/security/members/