-
Notifications
You must be signed in to change notification settings - Fork 5.2k
Always clear the local buffer in ArrayBuffer #49573
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Conversation
|
I couldn't figure out the best area label to add to this PR. If you have write-permissions please help me learn by adding exactly one area label. |
|
Tagging subscribers to this area: @dotnet/ncl, @vcsjones |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
LGTM
|
Are these tests generally broken? |
|
The mono ones are #49569. The coreclr osx ones I haven't seen. Can you open an issue for that? CI has been very unhappy the last few days. I suspect as a result things were merged that shouldn't have been, compounding the problem. |
|
this fix actually broke a test: |
|
Looks like something is calling WriteToConnection after Dispose @wfurt ? |
|
This is similar to #43686. We really should throw ObjectDisposed exception in this case. HttpClient with H2 is particularly prune to write after Dispose. I'll check if I can reproduce it locally with your change @davidfowl. I could not reproduce #43686 so it got eventually closed without resolution. I still feel the change make sense. We will just need to improve error checking inside SslStream. (or hold off like we do for the _nestedRead) |
|
Yes, the change does make sense. I was looking into the SSL APIs on OSX but I think that should be fixed separately. I'm gonna merge this, can you open an issue the write after dispose? |
If merging this is going to tank CI further, please don't. |
|
OK I pushed a new change that tries to keep the old behavior (writing into the ArrayBuffer after dispose), which should allow some slack for fixing the real use after free issue. We can revert that part of the change when we figure out why its happening on OSX. |
|
This change isn't critical to get in asap. Let's just prioritize finding and fixing the problem and hold on this until we do. |
|
I'm all for fixing the bug I don't want to hold this change hostage though. While it's not critical to get in ASAP, my only fear is that the bug will get punted and also the fix. At a bare minimum, if the fix for the real issue isn't trivial or the fix is hard verify (because reproducing is hard), we should take this improvement but I'll let @wfurt decide on what's best. Good news is that there's a dump captured as part of the crash... |
This change is causing a crash. While it should be valid, because of another issue it's not. We should fix the other issue before trying to push this in. And I do not want to complicate the code trying to mask the other issue. As I said, let's prioritize finding and fixing the other one, then this change will be valid and the original simple change can be merged. |
|
We generally agree, I just want to make sure we have some trip wires and backup plans in place (the other similar issue did get closed). But I'll be optimistic 😄 |
|
I think the real issue lives macOS PAL. I can reproduce it locally and I'll take look next week. |
|
Let me know if you want me to revert to the original change or if you want to take over this change in general and pair it with the OSX fix |
|
The workaround in the ArrayBuffer does not look 100% reliable due to race conditions. It will just make the crash to show up less often. Does it sound right? If it is the case, we should definitely wait for the proper fix. |
|
I'm not defending the workaround for the crash, it's as unreliable as it was before. The ArrayBuffer isn't thread safe without or without this change. |
|
As others have said, let's not merge a temporary work-around here. Let's fix the issue in thee OSX PAL or wherever and then merge the proper fix.
You've identified a nontrivial perf issue here, and the fix is straightforward. The odds of this getting punted are very low. |
|
Sounds fine to me |
|
/azp run runtime-libraries-coreclr outerloop |
|
Azure Pipelines successfully started running 1 pipeline(s). |
|
/azp run |
|
You have several pipelines (over 10) configured to build pull requests in this repository. Specify which pipelines you would like to run by using /azp run [pipelines] command. You can specify multiple pipelines using a comma separated list. |
|
/azp run runtime |
|
Azure Pipelines successfully started running 1 pipeline(s). |
|
/azp run all |
|
No pipelines are associated with this pull request. |
|
/azp list |
|
/azp run runtime-dev-innerloop |
|
Azure Pipelines successfully started running 1 pipeline(s). |
|
/azp run runtime-staging |
|
Azure Pipelines successfully started running 1 pipeline(s). |
|
How do I re-run these mono tests 😄 |
|
/azp run runtime-libraries-mono outerloop |
|
Azure Pipelines successfully started running 1 pipeline(s). |
- SslStream was holding onto a 4K byte[] after the handshake was complete. This was because the ArrayBuffer struct doesn't clear the local buffer field in dispose. This changes that.
2ce6a3c to
c1a7d45
Compare
|
Force push never fails... |

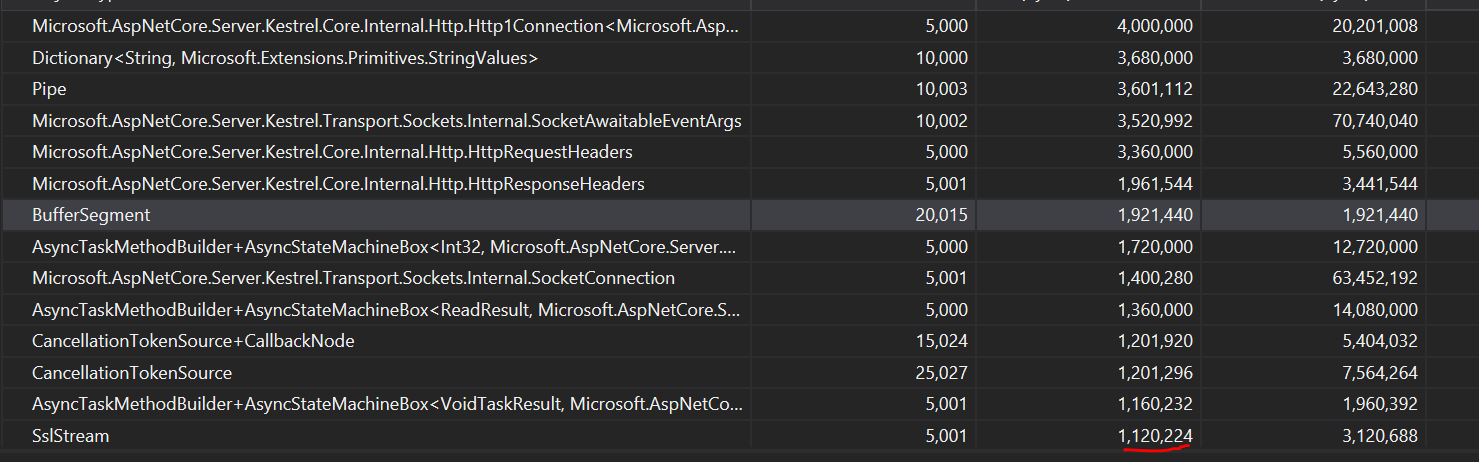
Before:

After:

Blocked on #49945