-
-
Notifications
You must be signed in to change notification settings - Fork 2.1k
Closed
Description
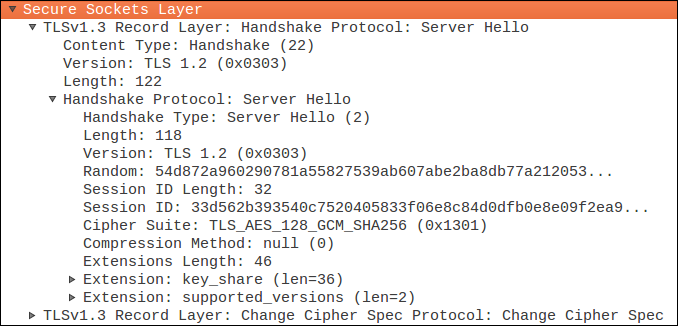
I found that I wasn't able to parse a Server Hello from the TLS 1.3 testing site https://enabled.tls13.com/ with the current development version of scapy (87916fd , Python 3, Linux).
Here's a snippet that reproduces the issue:
Code to reproduce
from scapy.all import load_layer
load_layer('tls')
data = bytes.fromhex(
'160303007a02000076030354d872a960290781a55827539ab607abe2ba8db77a212053ad'
'7e98c92598ba462033d562b393540c7520405833f06e8c84d0dfb0e8e09f2ea9d4e7b854'
'81b989ac130100002e00330024001d0020100b726fd77a0fd0e6a00228579d5e649f4105'
'1a9b2b59f5afb09fe72f793410002b000203041403030001011703030943359c1d734183'
'288f4c6141d07109241fde952af155d9b6162cf0db7a890322b650f66c54212d93d9bf2f'
'ac78bb2872e29a89b6ff3ef85d777f3dcb773ccaed62900908a2d310903cf22897d97ed9'
'e175596d78d4beb061ac6ed885f165ed443696c0ee6d9b5116ed09237e3f5beda2c1ff9f'
'f33e755ad84450ae9cf7763d3c6aec98eb6dff9c9753cb5a0c60d6f7b20bb7a45ae1e639'
'ae8a07c73db8db26b37c992f4d4ea7bec54715b696b463dbd5904b6d38bf69f9b4379d2a'
'bc101cdd5da07a21e4b1913ef5484c3d9b61b5c0abe6cb6dbaa9fbee0a81a4b3bd2aa744'
'9a4d3127f137b42191a635d8ec2b09a48f659656dae6ed246c1d8d9c8fced1b2a0a610d3'
'124410f32e9a4000b451a28ca3f1c02f705466bf8f6356cdec497471d78e4f785379ec71'
'468e8ac9dbce8bb29d249030929f4442003e3a67d4581d97f540e3309a2d8b3eb84b36ca'
'e9f9e78fb14e5401ff57cdcae2029e62875bc9d5bd9140ce8fae77dbf54495ef4cb4a0af'
'f591ad6f69eafab106db663adcc183722b62f03b1e273d17438a18be0880fab1c443d7b6'
'4746f33a5c57bf8f8ac3881ad47400b40f9d1b27e0c86012f2d3b18a5555610e772d3b51'
'711f591eaa1d5a6826a6390caa537d7db9511c208b668ea88b88c578a5b85cd8862e22b1'
'7b535156bd9093315b9cd0b47f76f1193d6e27440486dce42316dd342d942aad68e4b35e'
'31cf7a272a50a35f9fa00dc8f700a2ca981a32757dfa2a1ba0778c3308229e96b74ae350'
'751945c0286d35924b79763835a4bd05e8a6d2a632fff649615c8d8a1f73ad39b5c3478b'
'b6b4b4b6b21f26f4526ce710148d2ec37125de1ad72bada016c92c438a2d404a2ed0d246'
'21606509b8736cd3f99e387667dd23e15d56dc7ffbc3ec61825af7f08d633c7740655ea9'
'8fb0587a800fc74951b0a28b1724215c877a58a3f9b164edfd09b84508d8b3620413cdcc'
'2f88be147ff5c393fd2322b516547aae2e6dfcdd7d5ea36ef12b4f11c57c99ccde69d84a'
'3e08c85f57e1c907b1d9ba2cb011b05a518471d6484d5caddbb34070a7b720d561dec167'
'1f623e7f16f99897b7bc3f08f24ab00ece158e4bef897d3aca77d87c7fef27dd736fcd6c'
'8f0cfa7e42db6722bed9d88015afbe5ccdf4d17ce76122971fa4270d443eab4046724d79'
'1fca2355ca5aeba11f6881c05d4e47b55023aec41d297f744f2b0c23fe02ad1c245ebc78'
'972e3f6da0792911c793d0132327761e68758c3b5ce49f834de08e46c2c0284ffa2c7c6c'
'1ec20edfecd04872adba4bf046698e62361235ffc91738f7933bb7dbb65e6d206e747e9e'
'da02ddfcb1576a55c4a876df38b283aeb9cc965af8e67afa3bc19a66d208ee7fb1018f04'
'77ad6920bbafe294eb492c86af594adcef0b238a46f11f7c0e3a9c4b8f8db2feb8566f3f'
'87d9280a03b040fed551ebfeec95a6b7a163f043a209c16571893d61081afb797f3dff90'
'cd1261b086f64d2bbaaf80eff511d3b40549389d288827f758a620bf2dd7cd1e7ac1fa1d'
'08810fa595b12204286109b34b662d81759e6b36b300b56bb866b6bc4f9bc725f06d3aa2'
)
parsed = TLS(data)
representation = parsed.show()
print(representation)Wireshark knows that the first part of this is a Server Hello Handshake:
Unfortunately, Scapy doesn't:
###[ TLS ]###
type = application_data
version = TLS 1.2
len = 122
iv = b''
\msg \
|###[ Raw ]###
| load = "\x02\x00\x00v\x03\x03T\xd8r\xa9`)\x07\x81\xa5X'S\x9a\xb6\x07\xab\xe2\xba\x8d\xb7z! S\xad~\x98\xc9%\x98\xbaF 3\xd5b\xb3\x93T\x0cu @X3\xf0n\x8c\x84\xd0\xdf\xb0\xe8\xe0\x9f.\xa9\xd4\xe7\xb8T\x81\xb9\x89\xac\x13\x01\x00\x00.\x003\x00$\x00\x1d\x00 \x10\x0bro\xd7z\x0f\xd0\xe6\xa0\x02(W\x9d^d\x9fA\x05\x1a\x9b+Y\xf5\xaf\xb0\x9f\xe7/y4\x10\x00+\x00\x02\x03\x04"
mac = b''
pad = b''
padlen = None
It's getting the version and len, but not recognizing anything past that.
I can provide other captures if it helps?