-
Notifications
You must be signed in to change notification settings - Fork 2
Add support for RP-Initiated logout #32
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Conversation
auth-starter/src/main/java/com/vaadin/auth/starter/VaadinAuthContextImpl.java
Outdated
Show resolved
Hide resolved
|
There was some code shared with another branch which led to conflicts when merging with main, I'm converting this to draft until they're fixed. |
|
The PR is now ready for review. On top of the previous commits, it now has:
|
Is it planned to let this module stay open source? Or is it planned to change it later to closed source like done with the addition of the legacy components? I can totally understand the reasoning behind the license / payed model. But I personally think that security related code should stay open source to find and report security problems instead of forcing people to decompile it to find bugs or security holes. This comment comes from the fact that inline comments are used, which in turn are missing if close source is used and the source files aren't distributed. |
Hey @knoobie, thanks for the question! Current plan is to keep the sources open, although using the add-on or parts of the code will require a commercial license. |
That is totally valid! Thanks for the feedback, really appreciated! |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Initial comments.
auth-starter/src/main/java/com/vaadin/auth/starter/VaadinAuthProperties.java
Outdated
Show resolved
Hide resolved
auth-starter/src/main/java/com/vaadin/auth/starter/VaadinAuthProperties.java
Outdated
Show resolved
Hide resolved
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
The changes look good to me.
I was able to configure and see that the user's session is correctly removed when I was using it with Keycloak.
With Okta, I wasn't able to make it work, but because it fails with a CORS error when trying to reach the provider's API. I tried to configure it there, but not successfully. Judging by the format of the request, I believe it should work when properly configured.
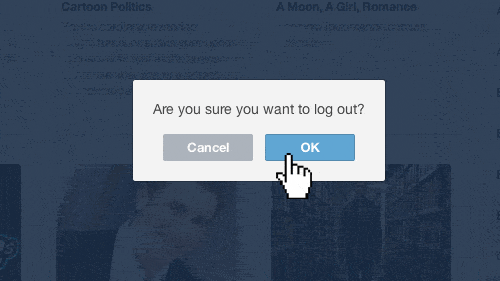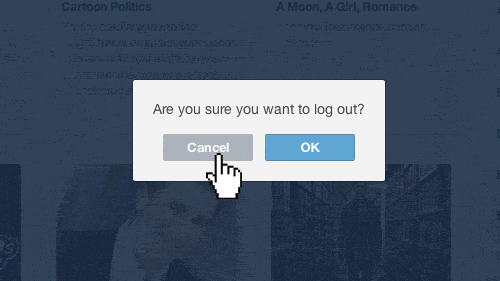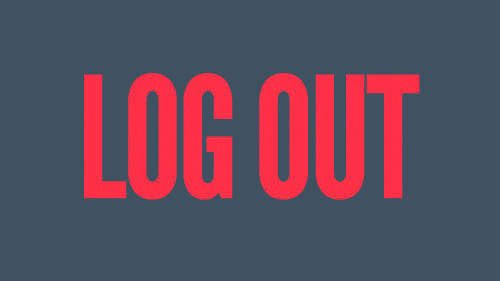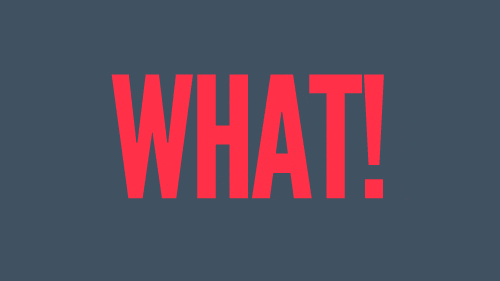
Description
VaadinAuthContextto handle the single sign-offFixes #24
Missing:
Type of change